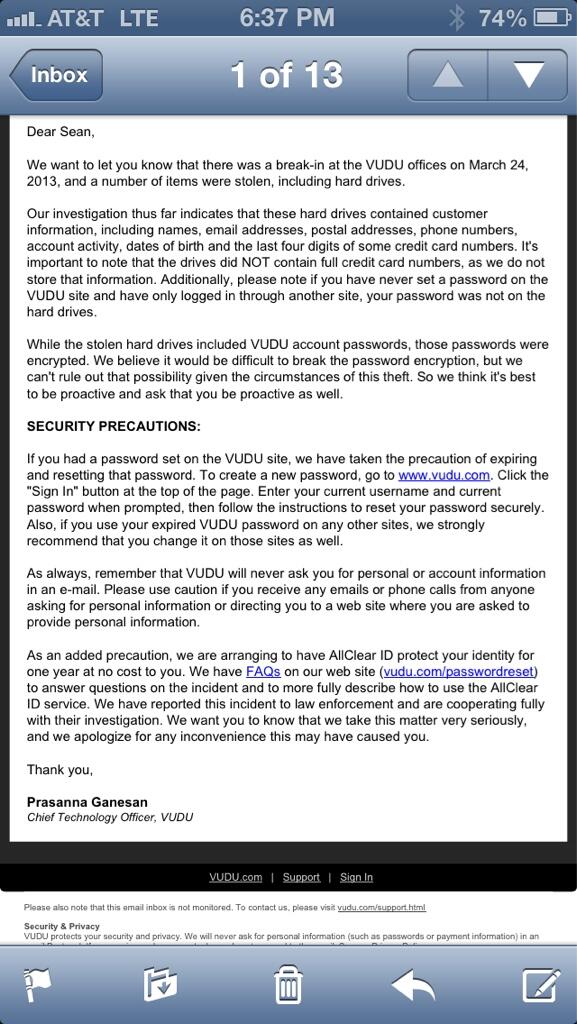
---**給我最愛的"奧巴馬總統"及防衞人們的隊伍,這些罪惡,你們看...**!!!
**USA/UK/TW/MACAU(FDZ)/KOREN/FR/UKN/PH/POLA/........All the world city lauguage**-
*
**--Please use Google with a
large family of God translator to translate your country / language city Oh ^ ^
--請各位用家善用谷歌大神的翻譯器,來翻譯你們的國家/城市的語言喔^^
--Por favor, use o Google com
uma grande familia de Deus tradutor para traduzir sua cidade pais / idioma Oh ^
^
--** - 국가 / 언어 시 를 번역하는 하나님 번역기 의 큰 가족과 함께 구글을 사용하십시오 아 ^ ^
--S'il vous plait utilisez
Google avec une grande famille de Dieu traducteur pour traduire votre ville de
pays / langue Oh ^ ^
--Bitte verwenden Sie Google
mit einer grosen Familie Gottes Ubersetzer zu Ihrem Land / Sprache ubersetzen
Stadt Oh ^ ^
--*** - あなたの国/言語の街を翻訳する神トランスレータの大きなファミリーでGoogleを使用してくださいああ^ ^
** - Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--** - Utilice Google con una
gran familia de Dios traductor para traducir tu ciudad país / idioma Oh ^ ^
** - Si prega di utilizzare
Google con una grande famiglia di Dio traduttore per tradurre la tua città paese / lingua Oh ^ ^
--Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--Bonvole uzu Google kun
granda familio de Dio tradukisto traduki via lando / lingvo urbon Ho ^ ^
http://translate.googleusercontent.com/translate_c?depth=2&hl=zh-CN&rurl=translate.google.com&sandbox=0&sl=auto&tl=zh-TW&u=http://www.theregister.co.uk/&usg=ALkJrhgsmWOoJskhJtzFi9vsqG8qFLsCbg
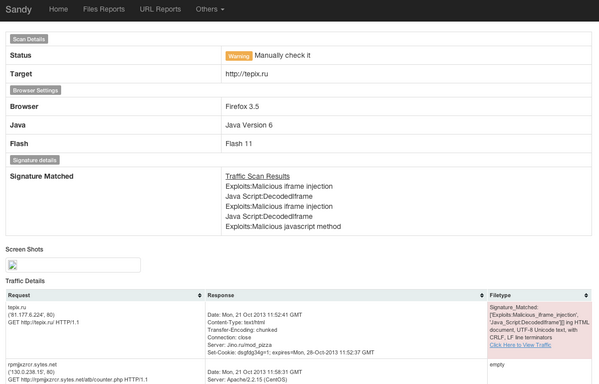
索尼否認PlayStation網絡抖動,儘管玩家抱怨
DDoS攻擊的債權膨脹在線
更新時間未知數量的玩家已經拉開序幕索尼的PlayStation網絡,但該公司將繼續堅持其服務是穩定的。
張貼在社交媒體傳聞卻出現講一個不同的故事。
有些客戶正在說他們正在看到一個消息,上面寫著:“網絡正在維修”
其他人,同時,正在未經證實的聲稱,PlayStation網絡正在遭受拒絕服務(DDoS)攻擊。
@PlayStation網下來了! 聽到的Xbox 1唯一的好東西。 整理出來的索尼,我切換到黑暗的一面
約翰-道爾(@JohnLfcdoyle) 2014年8月24日
 Tom
@Toms_Yorkshire
Follow
Tom
@Toms_Yorkshire
Follow
This happens when psn is down and it says connecting to sony network and then asks you to sign in #bluescreenofdeath
 Thought Lateral
@ThoughtLateral
Follow
Thought Lateral
@ThoughtLateral
Follow
Breaking news: Sony PlayStation Network down. Lizard squad hackers claim responsibility. @TheRegister
DownDetector也同樣指出在明顯的網絡衝突的PSN遊戲玩家大穗。
在其支持網站的官方聲明中 ,索尼表示:
我們知道,一些用戶遇到困難享受PSN。 我們已經確認了PSN的是穩定的。 如果您有問題,我們建議您聯繫您的Internet服務提供商。該公司將繼續要求其當前的網絡狀態為“在線”。 然而,該頁面還稱這是一次更新是在8月15日。
另外,索尼的維修安排在週一 ,這可能會影響誰的英國人都希望明天白天PSN上玩看到,因為它是一個公眾假期Blighty。
的註冊要求索尼告訴我們更多關於報告其用戶群的網絡抖動,但科技巨頭是尚未得到反饋給我們在發布的時候。 我們會更新這個故事,如果我們聽到更多。
你努力進入PSN的權利嗎? 請告訴我們更多在評論部分。 ®
更新
索尼在線娛樂公司的老闆已經咳嗽了一聲到“大規模分佈式拒絕服務攻擊”。 故事在這裡 。===========================================
射擊em起來:索尼在線娛樂公司遭遇“大規模分佈式拒絕服務攻擊”
破壞作為公司遊戲的鬥爭,以控制網絡
索尼正在遭受的拒絕服務的主要分佈式攻擊的網絡中,該公司的在線娛樂老闆今天證實。
它配備後的註冊 報告有關PlayStation網絡(PSN)上的服務擺動抱怨剛才在週日。
國有企業的負責人John史沫特萊咳了一聲,被DDoSed一系列的鳴叫,投訴後小時週末遊戲玩家誰是不能訪問PSN浮出水面索尼。
他還表示,他的美國航空公司362航班已經改行 “出於安全原因” -剛過歹徒暗示官員的爆炸物是船上。
在拒絕服務分佈式攻擊,史沫特萊告訴微博:
史沫特萊提供一個鏈接到地圖上表示將DDoS攻擊擊中。 然後,他在推特上說,他將失去聯繫的國內航班三小時。
的PlayStation承認有其服務的問題,但並未提及在鳴叫它貼在最後一小時內的DDoS攻擊。
“網絡更新:我們的工程師都知道的問題,正在努力解決這些問題,我們會及時向大家發布-很抱歉給您帶來不便,”它說 。 ®
 John Smedley
@j_smedley
Follow
John Smedley
@j_smedley
Follow
We are under attack by a large scale ddos. Being dealt with but it will impact games until its handled.
 John Smedley
@j_smedley
Follow
John Smedley
@j_smedley
Follow
======================
 John Smedley
@j_smedley
Follow
John Smedley
@j_smedley
Follow
Services will be gradually restored. For
some it's up now. For others the route they take may be flooded so they
can't log in yet.
 John Smedley
@j_smedley
Follow
John Smedley
@j_smedley
Follow
========================
 John Smedley
@j_smedley
Follow
John Smedley
@j_smedley
Follow
The problem is upstream of our network we have no control. So they are flooding the routes to us too. That's how it works.
http://translate.googleusercontent.com/translate_c?depth=2&hl=zh-CN&rurl=translate.google.com&sandbox=0&sl=auto&tl=zh-TW&u= http://www.theregister.co.uk/Author/2553&usg=ALkJrhgS2HsIU4hHXHubG3U99DoaXnXB9w
============================================##########
“索尼和抽搐,”黑客船員蜥蜴隊:“我們不干”
媽呀,聯邦調查局 *咳*我們做了我們所要做的
蜥蜴隊黑客船員似乎已經稱為繼它退出週末高調攻擊索尼以及對暴雪和抽搐,廣播平台,
為遊戲玩家在線攻擊,等等。
騙子黑客八強小組公佈了他們的意圖扔在他們的lizardsquad.com網站上的毛巾(和Pastebin複製的通知在這裡 )。 該通知- 小盜賊被吊死,但偉大的人逃脫 -充滿夸父讓人想起LulzSec的幾年前的那種。
大約在同一時間上週六,該集團的官方Twitter帳號被用來聲稱兩名成員已被銬了聯邦調查局。 “看來聯邦調查局已經得到科莫多和鬣蜥,現在,我想我下一步。
祝你好運FBI”的更新說明。 此消息是由增編反駁到:“我們退出”的lizardsquad.com網站,
其中規定“獎愚蠢的新聞網站通知去:INCGAMERS.COM對於自己明確的愚蠢居然以為這個網站是siezed [原文]和信[原文]我們已經被逮捕。“
聯邦當局避談逮捕任何人通過歸因於蜥蜴隊高調的黑客,所以我們顯然有一個不可靠敘述者在這裡處理。
蜥蜴隊似乎已經消失了安靜了幾天,至少求愛的宣傳與後問我什麼 Reddit上剛在上週。
這種沉默,甚至該集團表示決定解散可能被解釋為通過努力回應了對手活動家/遊戲玩家,
激進革命 ,網上跟踪下來,DOX他們。
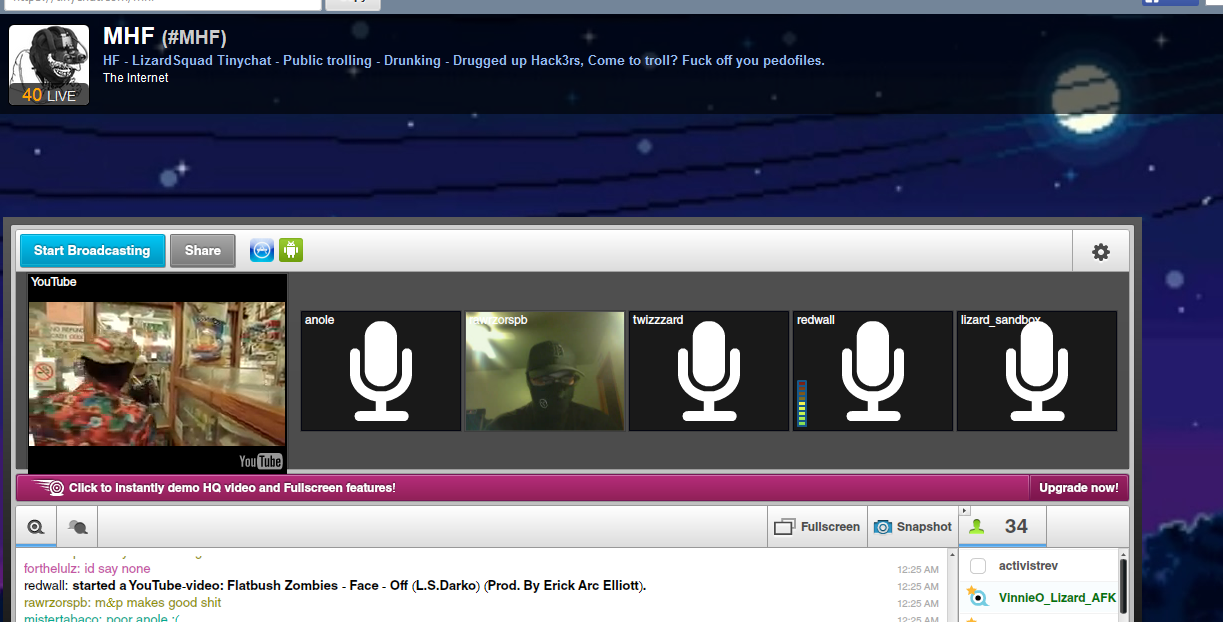
蜥蜴隊上升到突出與所聲稱的攻擊對索尼的PlayStation網絡在上個月,據說扔一些遊戲玩家關閉系統。 索尼最初聲稱承認,它曾經被它的網絡是穩定的打了一個強大的DDoS攻擊。
大約在同一時間,索尼在線娛樂公司的老闆約翰·史沫特萊在美國的航班被改後的蜥蜴隊錯誤地警告說有可能是船上的炸藥。 ®
為遊戲玩家在線攻擊,等等。
騙子黑客八強小組公佈了他們的意圖扔在他們的lizardsquad.com網站上的毛巾(和Pastebin複製的通知在這裡 )。 該通知- 小盜賊被吊死,但偉大的人逃脫 -充滿夸父讓人想起LulzSec的幾年前的那種。
我們2個星期前載我們的行程與計劃的遊戲社區造成嚴重破壞。 我們的動機改變整個冒險。 最初它是為了看看我們是否能逃避被抓,體驗原始的快感無政府狀態,而不是被綁定到假冒的法律。 我們一直在呼籲一切從有組織犯罪“團伙”來完成混蛋,真是我們只是太多的空閒時間幫傢伙。OMG聯邦調查局
縱觀我們的旅程,我們遇到新的人,獲得了新的成員,學到了新的東西。 人們試圖採取搖擺在美國(和遺漏)。 我們證明,即使我們是小本非常大的世界裡,一小群朋友誰一起工作可能會導致很多混亂無法律後果。 今天我們將要解散,綠色爬行動物和其他廢話之後,我們的生活信不信由你,要做的事情,人們見面。
再見。
大約在同一時間上週六,該集團的官方Twitter帳號被用來聲稱兩名成員已被銬了聯邦調查局。 “看來聯邦調查局已經得到科莫多和鬣蜥,現在,我想我下一步。
祝你好運FBI”的更新說明。 此消息是由增編反駁到:“我們退出”的lizardsquad.com網站,
其中規定“獎愚蠢的新聞網站通知去:INCGAMERS.COM對於自己明確的愚蠢居然以為這個網站是siezed [原文]和信[原文]我們已經被逮捕。“
聯邦當局避談逮捕任何人通過歸因於蜥蜴隊高調的黑客,所以我們顯然有一個不可靠敘述者在這裡處理。
蜥蜴隊似乎已經消失了安靜了幾天,至少求愛的宣傳與後問我什麼 Reddit上剛在上週。
這種沉默,甚至該集團表示決定解散可能被解釋為通過努力回應了對手活動家/遊戲玩家,
激進革命 ,網上跟踪下來,DOX他們。
蜥蜴隊上升到突出與所聲稱的攻擊對索尼的PlayStation網絡在上個月,據說扔一些遊戲玩家關閉系統。 索尼最初聲稱承認,它曾經被它的網絡是穩定的打了一個強大的DDoS攻擊。
大約在同一時間,索尼在線娛樂公司的老闆約翰·史沫特萊在美國的航班被改後的蜥蜴隊錯誤地警告說有可能是船上的炸藥。 ®
21評論
###############################################################
=========
RPHOTO:正義的婦女受害者#PoliceBrutality ! #APDProtest #DOJAPD #OpAlbuquerque #FTP #FixThePolice HTTP:// twitpic.com/e2gfla
http://redd.it/2evyx9
按照我們在Twitter! @reddit_AMA |請看看我們的規則及常見問題解答
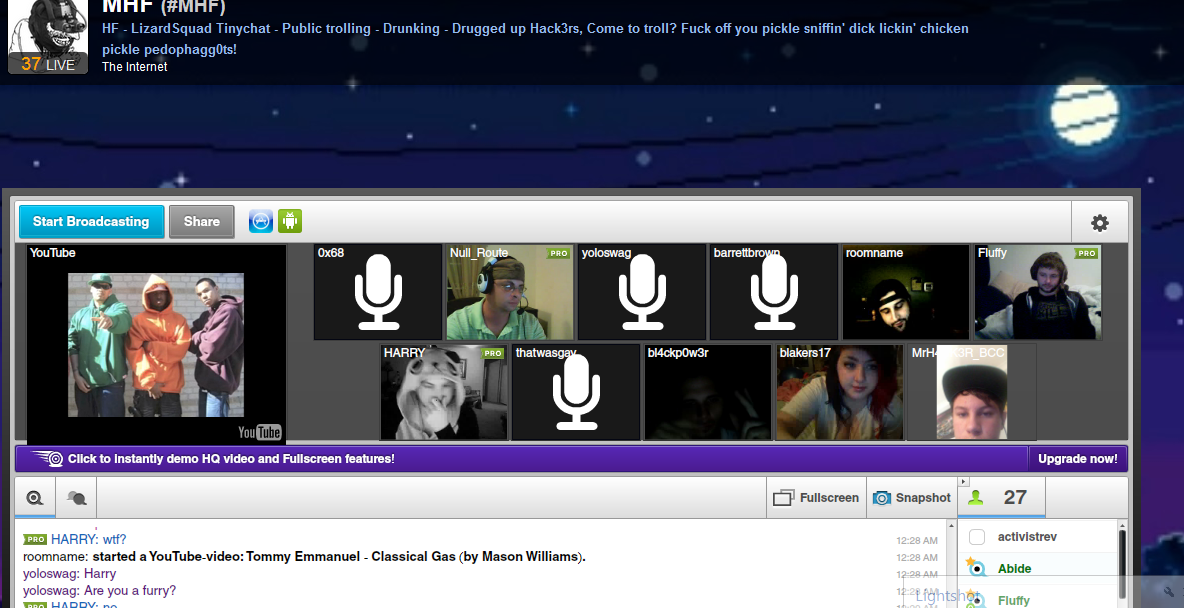
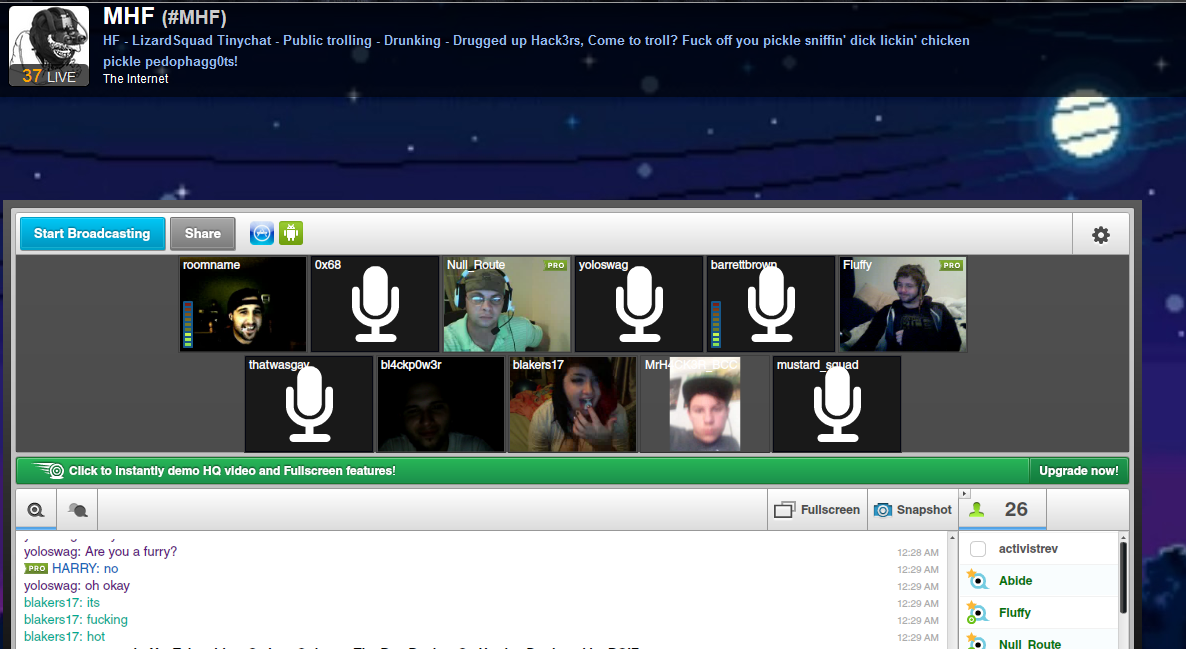
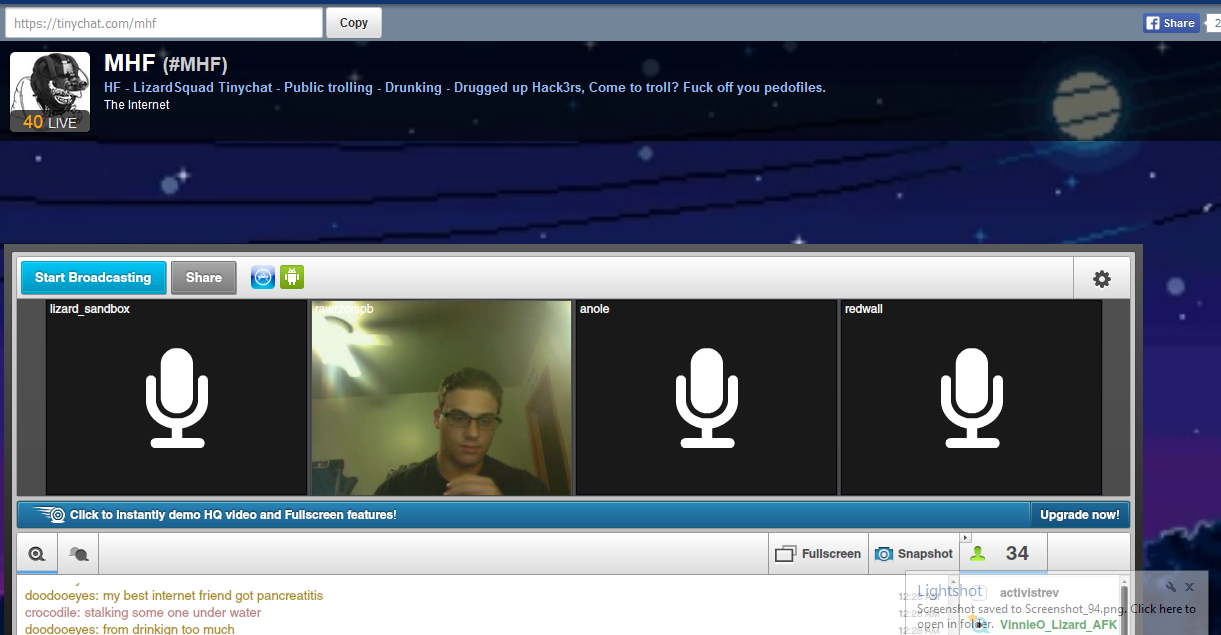
提交 通過LizardSquad
http://translate.googleusercontent.com/translate_c?depth=2&hl=zh-CN&rurl=translate.google.com&sandbox=0&sl=auto&tl=zh-TW&u= http://www.reddit.com/r/IAmA/comments/2evyx9/we_are_lizardsquad_ask_us_anything/&usg=ALkJrhiza3rHNMuvarkRrwj5So-8zTgjqg
============
前200名的評論 顯示500
蜥蜴隊
@ LizardSquad
911。 時間在流逝。
irc.lizardsquad.com
加入時間2011年11月
看的像@ j_smedley的飛行被重定向,我們呼籲所有蜥蜴#PrayForFlight362 。 pic.twitter.com/J9xAZEPSJT

###################################################################
#######################################################################
#######################################################################
**--Please use Google with a
large family of God translator to translate your country / language city Oh ^ ^
--請各位用家善用谷歌大神的翻譯器,來翻譯你們的國家/城市的語言喔^^
--Por favor, use o Google com
uma grande familia de Deus tradutor para traduzir sua cidade pais / idioma Oh ^
^
--** - 국가 / 언어 시 를 번역하는 하나님 번역기 의 큰 가족과 함께 구글을 사용하십시오 아 ^ ^
--S'il vous plait utilisez
Google avec une grande famille de Dieu traducteur pour traduire votre ville de
pays / langue Oh ^ ^
--Bitte verwenden Sie Google
mit einer grosen Familie Gottes Ubersetzer zu Ihrem Land / Sprache ubersetzen
Stadt Oh ^ ^
--*** - あなたの国/言語の街を翻訳する神トランスレータの大きなファミリーでGoogleを使用してくださいああ^ ^
** - Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--** - Utilice Google con una
gran familia de Dios traductor para traducir tu ciudad país / idioma Oh ^ ^
** - Si prega di utilizzare
Google con una grande famiglia di Dio traduttore per tradurre la tua città paese / lingua Oh ^ ^
--Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--Bonvole uzu Google kun
granda familio de Dio tradukisto traduki via lando / lingvo urbon Ho ^ ^
===> Control Principle
"In the iis or apach point to add illegal content domain, the domain name point to the standard 404 error output.
Unauthorized domain can be controlled and the IP, in order to achieve control of the domain name registration request. "
iis point standard 404
Simply put the site files in the directory can be deleted.
apach point standard 404
By modifying the httpd.conf
Delete the # sign in front of a standard can be reported error message. When the name appears in ip access content directly inconsistent filing requirements
#ErrorDocument 500 "The server made a boo boo."
#ErrorDocument 404 /missing.html
#ErrorDocument 404 "/cgi-bin/missing_handler.pl"
#ErrorDocument 402 http://www.example.com/subscription_info.html
========###########################################################
--- Alternate [optional]:
1) Keep alive, and other performance-related:
a) sendfile on
Allow sendfile system call, to avoid sending data through the memory buffer overhead.
b) tcp_nodelay on
Open the TCP stack assistance TCP_NODELAY option to disable nagle buffer algorithm, making the service sends data immediately, rather than waiting and then send the data after a certain amount of size. The need for immediate corresponding request service or a small file to open more static service recommendation.
:
2) refuse the request url contains <"\ \ 0 other harmful character. These characters in a normal GET request does not appear in the basic, but often used by hackers to complete scripting attacks, the use of such a rule similar to the simple url firewall , a lot can ease extent reflective cross-site scripting attacks and other attacks from the url.
Configuration: Configure the location segment:
if ($ request_uri ~ * (\ '| \ <| \ "| \% 00 | \% 22 | \% 27 | \% 3e | \% 3c | \>)) {
(. *) rewrite http: // $ host: $ server_port / redirect;
}
Note that since this configuration will shield the request of the special characters, so the needs and product lines RD confirmed before use does not affect the normal request.
Enforcement measures:
Delete the existing configuration item autoindex on; configuration
In the server segment added:
location ~ * \. (sql | bak | inc | old) $
{
return 403;
}
For file upload function nginx, need to server segment for file upload directory (such as / upload /) as follows
location ^ ~ / upload / {
if ($ request_filename ~ * \ (jpg |!. jpeg | gif | png | swf | zip | rar | txt) $) {
return 403;
}
alias / home / work / path / to / upload /;
}
Segment in the global configuration:
events {
use epoll;
worker_connections 51200;
}
worker_rlimit_nofile 51200;
Use the following command to start nginx nginx startup script in:
limit -n 65535 sbin / nginx
And is the main limit tools should be root, and open the s flag.
-rwsr-sr-x 1 root root 33871 Dec 4 2006 / bin / limit
Configuring the server segment
server_tokens off;
more_set_headers 'Server: Apache';
error_page 400 403 404 500 501 502 503 504 505 /tb/error.html;
# / tb / error.html can be configured to your own error pages as needed product line
if ($ host ~ "\ .domain \ .com $ | \ .domain \ .com \:! | \ .domain \ .com \ .cn $ | \ .domain \ .com \ .cn \: | \ .domain \ .cn $ | \ .domain \ .cn \: |... ^ \ d {1,3} \ \ d {1,3} \ \ d {1,3} \ \ d {1,3} $ | ^ \ d {1,3} \ \ d {1,3} \ \ d {1,3} \ \ d {1,3} \:... ")
{
rewrite ^ / $ http://error.domain.com/errorname.html?url=%1&fr=xxx redirect (*.);
}
# If the product lines within its own domain name or IP confirmed the company can point to a third party domain name is not in the above regular expression matching range, please add your own
# Where, xxx represents product lines, such as image, news, etc.
# For use NOAH semantic monitoring nginx, if the monitoring request HOST field (or fields do not meet the above rules HOST) is not included, the monitoring request will be redirected. Please specify the product line in the monitoring request HOST field when configuring the monitoring of relevant semantic domain nginx is located.
If there nginx-status page, you need to add the following global configuration:
location / nginx-status {
stub_status on;
access_log off;
allow 127.0.0.1; # here can be configured for other machines within the network IP addresses, but can not be configured as the external network or office network address
deny all;
}
In the location section configuration:
if ($ request_uri ~ * (\ / \ svn \ / |. CVS \ / Entries)) {
(. *) rewrite http: // $ host: $ server_port / redirect;
}
=================
/
#################
-- *备选[可选]:
1) Keep alive和其它性能相关:
a) sendfile on
允许sendfile系统调用,避免经过内存缓冲区发送数据的开销。
b) tcp_nodelay on
打开TCP协助栈中的TCP_NODELAY选项,禁用nagle缓冲算法,使得服务端立即发送数据,而不是等待数据量达到一定大小之后再发出。对于需要即时相应请求的服务或小文件较多的静态服务推荐打开。
:
2) 拒绝url里包含< ” \ \0等有害字符的请求。这些字符在正常的GET请求里基本不会出现,但是经常被黑客用来完成脚本攻击,采用这样的规则类似于简单的url防火墙,很多程度上可以缓解反射型的跨站脚本攻击和其他来自于url的攻击行为。
配置方法:在location段中配置:
if ($request_uri ~* (\'|\<|\"|\%00|\%22|\%27|\%3e|\%3c|\>)) {
rewrite (.*) http://$host:$server_port/ redirect;
}
注意,由于此配置会屏蔽请求中的特殊字符,因此需要和产品线RD确认不会影响正常请求后方可使用。
执行办法:
删除配置项中已有的autoindex on;配置
在server段中加入:
location ~* \.(sql|bak|inc|old)$
{
return 403;
}
对于有文件上传功能的nginx,需要在server段中对于文件上传目录(如/upload/)作如下配置
location ^~ /upload/ {
if ($request_filename !~* \.(jpg|jpeg|gif|png|swf|zip|rar|txt)$) {
return 403;
}
alias /home/work/path/to/upload/;
}
在全局段中配置:
events {
use epoll;
worker_connections 51200;
}
worker_rlimit_nofile 51200;
在nginx的启动脚本中使用如下命令来启动nginx:
limit –n 65535 sbin/nginx
且limit工具的属主应为root,并且打开s标志位。
-rwsr-sr-x 1 root root 33871 Dec 4 2006 /bin/limit
在server段中配置
server_tokens off;
more_set_headers 'Server: Apache';
error_page 400 403 404 500 501 502 503 504 505 /tb/error.html;
#/tb/error.html可根据产品线的需要配置为自己的错误页面
if ($host !~
"\.domain\.com$|\.domain\.com\:|\.domain\.com\.cn$|\.domain\.com\.cn\:|\.domain\.cn$|\.domain\.cn\:|^\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}$|^\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}\:")
{
rewrite ^/(.*)$ http://error.domain.com/errorname.html?url=%1&fr=xxx redirect;
}
#若产品线自有的域名或确认可以指向公司IP的第三方域名不在上面正则式匹配的范围之内,请自行添加
#其中,xxx表示产品线,如image,news等
#对于使用NOAH进行语义监控的nginx,如果在监控请求中未包含HOST字段(或HOST字段不符合上述规则),则监控请求会被重定向。请产品线在配置相关语义监控时在监控请求中指定HOST字段为nginx所在的域名。
如果存在nginx-status页面,需要加上如下全局配置:
location /nginx-status {
stub_status on;
access_log off;
allow 127.0.0.1; #此处可配置为其它内网机器IP地址,但不能配置为外网或办公网地址
deny all;
}
在location段中配置:
if ($request_uri ~* (\/\.svn\/|CVS\/Entries)) {
rewrite (.*) http://$host:$server_port/ redirect;
}*======================================
/
=====================================
*IIS is not easy to close the record domain names point
Internet management more standardized, there is no record in the domestic domain name on the Internet are to disappear.
Some of the individual owner of the domain name is open pan-domain solution, so you can not directly close the ip access. Now with an alternative recourse.
1 Create a virtual host in iis
2 Host header wrote on the domain name to be closed
3 points is empty, usually let him out of 404 or 403 error.
=====
----- 360 security guards steal my bandwidth !!!?
("Chinaman's theft of privacy, global human also know that China refuses to recognize the lies, the world's self Yukai Ming's Chinese communism, really ugly, hybrid hard into people, leaving hundreds of millions of people of all victims, jerk!")
When we check the server bandwidth usage stumbled over 9M (Internet Data Center m176.net installed on the server made masterpiece 360, they are able to achieve 9M even more bandwidth), and then simply do not open any business. 360 security guards in the "flow control" found in the extensive use of bandwidth is 360 program yourself, being uploaded data, large bandwidth to 9M. In order not to affect the normal course of business, check (NIC -> Advanced -> Settings -> Exceptions) found that "360 security guards real-time protection" before the check, here there is a "liveupdate 360" is the same checked. If this is the case only, we can not let him get rid of these by checking on the rumor when the server data on the line.
Dramatic problem arises. You put 360 closed, then open, "360 security guards real-time protection" This option is automatically selected on the hook again. This means that 360 first put the card on fire on the election, so that their programs can freely use my computer's bandwidth.
If your computer is turned on Microsoft's own fire (NIC -> Advanced -> Settings -> General -> Enable) to use other programs such as BT Thunder QQ and other programs (windows xp windwos 2003) will pop-up "do you want to keep Blocker K ". If you choose to keep blocking, that is to say not transfer data outside the initiative; select "Unblock (U)" you can let the program take the initiative to communicate outwards. If your machine is in use iis apach need to provide external Internet services, such as the words of that nature would have selected "Unblock (U)", but I do not want to let him 360 Foreign Service Yeah. I just let him on my computer services, but also did not say it to other people and services.
Estimated to be 360 (main version: 7.7.0.2001 spare Trojans Library: 2011-04-03) application in the background provides a procedure similar to BT download upgrades to other 360 users, whether there are other data on the inside run, we do not know . Even so you have to give me to say it, but the card can not be directly applied to the fire in his own way. Is there anything different with the hackers out? Is this the cost free to pay it? Under the banner name of security can not be like the "rogue" doing the same thing it unsafe.
Trojans fall according to the most special thing to be a dry 360 to learn how to make use of. 360 I still continue to use, but when not necessary, do not open or less open it. He was no longer waiting for a mature kind of computer use when we talk about it. Development of free software be sure to take care of themselves veterans door, do not do like 360 so this feature too unkind.
The following software have been tested for without this "rogue" work can be. They also want the users to contribute bandwidth out, the system will let the user choose the fire rather than in the back so underhand.
Storm Music video Tencent QQ cool music box Thunder testing other software users own it.
Long original site please indicate the source (m176.net dragon)
##################################################
---**IIS 簡易關閉未備案域名指向**----
互聯網管理越來越規範,在國內沒有備案的域名都是要在互聯網上消失的。
有些機主的個別域名又是開了泛域名解,這樣就無法直接關閉ip訪問。 現在用個變通的法子。
1.在iis 新建一個虛擬主機
2.主機頭里就寫上要關閉的那個域名
3.指向的內容為空,一般是讓他出404 或403錯誤。
==========================================
**IIS|apach 阻止域名指向,顯示標準404錯誤**
===>控制原理
"在iis或apach裡添加非法指向域名,域名的內容再指向標準404錯誤輸出。
可以對未授權的域名及IP進行控制,以達到域名備案控制的要求。"
iis指向標準404
只需把網站目錄裡的文件刪除即可。
apach指向標準404
通過修改httpd.conf
刪除出前面的#號就可以報出標準的出錯信息。 以名ip訪問時直接出現不符備案要求的內容
#ErrorDocument 500 "The server made a boo boo."
#ErrorDocument 404 /missing.html
#ErrorDocument 404 "/cgi-bin/missing_handler.pl"
#ErrorDocument 402 http://www.example.com/subscription_info.html
========================================
-----360安全衛士偷用我的帶寬!!!?
( "支那人的偷竊私隱,全球人類也知道,死不承認的中國謊言,全世界自喻開明的中國共產,真醜惡,雜種難以變成人,遺害億萬人們的所有,混球!")
我們檢查服務器時偶然發現帶寬使用超過9M(互聯網數據中心m176.net 服務器上安裝國產大作360,所以能達到9M 甚至更多帶寬),而這時根本就沒有開任何業務。 用360 安全衛士中的“流量監控”發現在大量使用帶寬的程序正是360自己,正在上傳數據,帶寬大至9M。 為了不影響正常業務,檢查(網卡->高級->設置->例外)發現“360安全衛士實時保護” 前勾選了,下面還有一個“liveupdate 360" 也是一樣勾選了。 如果僅是這樣的話,我們可以把這些勾選去掉讓他不要當服務器對外傳數據就行了。
戲劇性的問題出現了。 你把360 關了,再打開,“360安全衛士實時保護”這個選勾又自動選上了。 意思是說360 首先就要把網卡防火選上,讓自己的程序可以隨意使用我電腦的帶寬。
如果你的電腦已開啟微軟自帶防火(網卡->高級->設置->常規->啟用)使用其它程序如BT 訊雷QQ等程序(windows xp windwos 2003)都會彈出“你想保持阻止程序嗎K ” 。 如果選保持阻止,那就是說不能向外主動傳數據;選“解除阻止(U)”就可以讓程序向外主動通訊。 如果你的機是在使用iis apach 等需要對外提供互聯網服務的話那自然就得選”解除阻止(U)”,可是我的360不想讓他對外服務呀。 我只要讓他對我的電腦服務,沒說還要向其它人服務吧。
估計是360(主程序版本:7.7.0.2001 備用木馬庫:2011-04-03)在後台向其它360用戶提供了類似BT 下載升級程序方面的應用,是否有其它數據在裡面跑,我們不得而知。 就算是這樣你也得給我說一聲呀,更不能直接把自己加到網卡防火裡呀。 這與黑客有什麼不同了呢? 難道這就是免費需要付出的代價嗎? 打著安全的旗號也不能像“流氓”一樣做不安全的事吧。
特落依木馬最要幹的事怎麼讓360學來用了。 360 我還是繼續用,只是沒必要時就不要開或少開吧。 等待他成熟得不再利用我們善良的電腦時再說吧。 開發免費軟件的老總門千萬要保重身體,別像360這樣這個功能做得太不厚道。
對下面的軟件進行測試沒有這個“流氓”工能。 他們也想讓用戶把帶寬貢獻出來,系統防火會讓用戶自己選擇而不是在背後使陰招。
暴風音影騰訊QQ 酷我音樂盒訊雷其它軟件網友自己測試吧。
本站長原創轉載請註明出處(m176.net 火龍)
##################################################
---Secret Chinese special forces tactical sign language
---揭秘中國特種部隊戰術手語
"[Assembly] is only able to act decisively in any condition, one bold action in order to achieve victory. Our descendants would rather forgive mistakes actions, are opposed to doing nothing. - Guderian.
Special forces in combat because of the environment in particular, tend to rely on mutual communication is silent language: Tactical sign language. Tactical sign language, through specific hand gestures, body movements and facial expressions, transmit specific information directing action by the forces themselves can develop.
[集结号]只有能在任何条件下当机立断、大胆行动的人,才能取得胜利。我们的后代宁肯原谅错误行动,也不赞成无所作为。——古德里安.
特种兵在实战中由于所处的环境特殊,相互间的沟通往往依靠的是无声语言:战术手语。战术手语,是通过特定的手形、手势、形体动作和面部表情,传递特定信息指挥行动,可由各部队自行制定。"

'On a parade ground in Shenzhen, Levin played in a series of tactical training in sign language: a gun, killing, tear gas, cover (make-up photos, followed by the upper left, upper right, lower left, lower right)
''在深圳某練兵場上,李文在訓練中打出一連串戰術手語:有槍、殺害、催淚氣體、掩護(拼版照片,依次為左上、右上、左下、右下)
=====

He is not a police officer, but to cultivate the 28 police officers; not only their own to take the first, but also bring out the 51 first; as a good squad, he has brought out 410 squad leader, he is the agent of Guangdong Frontier Corps Tactical Brigade platoon leader, four sergeants long Levin. 13 years of military let Levin trained an excellent skills, he has won 31 times above the provincial military contest first. In 2007 the National Border contest, only junior high school culture Levin in the two months before the temporary new sign language contest tactical race, topped, won the crown. Back troops from the arena, Levin in mastering the tactical knowledge of sign language based on the combination where the forces responsible for the smuggling, narcotics and other tasks, and innovation to more than 100 sets of novice language, a "sign language" Bing Wang National Border system.
他不是警官,但培育了28名警官;不僅自己拿第一,還帶出51個第一;作為一名好班長,他先後帶出410名班長,他就是廣東邊防總隊機動支隊代理排長、四級警士長李文。 13年軍旅讓李文練就了一身過硬本領,他先後31次勇奪省級以上軍事比武第一名。在2007年全國邊防大比武中,僅有初中文化的李文在賽前兩個月臨時新增的戰術手語比武競賽中,技壓群雄,勇奪桂冠。從賽場上回到部隊,李文在掌握戰術手語知識基礎上,結合所在部隊擔負的緝私、緝毒等任務,又創新出100多套新手語,成為全國邊防系統的“手語”兵王。
On a parade ground in Shenzhen, Li (right) led his comrades tactical training in sign language
在深圳某練兵場上,李文(右)帶領戰友訓練戰術手語
'' A 'arrest drug traffickers' operations in the mountains of the exercise is being carried out quietly in Shenzhen, Li (right) led his comrades toward the goal.
''一場“抓捕毒販”行動演練正在深圳叢山中悄然進行,李文(右)帶領戰友撲向目標.
========================================================================
Here is the famous anti-terrorist troops - German GSG-9 Border Police troops fighting in sign language,
The sign language is common in Western countries fighting in sign language, is reproduced below for reference.
Famous anti-terrorist troops - German GSG-9 Border Police troops fighting in sign language
An adult -------- arms stretched out to the side, raised his hand to his arm height, palm down.
2 children -------- arms stretched out to the side, elbows bent, palms down on the fixed waist.
Three female suspects - palm toward his chest, fingers apart is bowl-shaped, meaning that women's breasts.
4 Hostages -------- hand stuck his neck, the implication is taken hostage.
5 Commander ------ index finger, middle finger, ring finger side by side straight, horizontal on the other arm.
在深圳野外的一次訓練中,李文(前)打出“停止”的戰術手語(左一)
下面介紹的是著名的反恐怖部隊——德國GSG—9邊境警察部隊的戰鬥手語,
該手語也是西方各國通用的戰鬥手語,現摘錄如下,僅供參考。
著名反恐怖部隊――德國GSG-9邊境警察部隊的戰鬥手語
1成人--------手臂向身旁伸出,手部抬起到胳膊高度,掌心向下。
2小孩--------手臂向身旁伸出,手肘彎曲,掌心向下固定放在腰間。
3女性嫌疑犯--掌心向著自己的胸膛,手指分開呈碗狀,寓意是女性的胸部。
4人質--------用手卡住自己的脖子,寓意是被劫持的人質。
5指揮官------食指、中指、無名指並排伸直,橫放在另一手臂上。=========================================================
6 straight thumb and forefinger -------- pistol, each 90 degrees, was pistol posture.
7 automatic weapons ------ grasping fingers bent into shape, sweep up and down in front of his chest, like playing the guitar the same.
8 shotgun -------- signals are armed with shotguns players, just with the index finger pointing their weapons can be.
9 --------- door with the index finger upward from the left and then down below, make a rectangular opening gesture, on behalf of the shape of the door.
10. windows -------- with the index finger from the bottom up, right, down and then left to make a closed rectangle gesture.
6.手槍--------伸直大拇指及食指,互成90度,呈手槍姿勢。
7.自動武器------手指彎曲成抓狀,在胸膛前上下掃動,像彈奏吉它一樣。
8.霰彈槍--------發信號的是手持霰彈槍的隊員,只需用食指指指自己的武器便可。
9.門口---------用食指由下方向上,向左再向下,作出開口矩形的手勢,代表門口的形狀。
10.窗戶--------用食指由下向上,向右,向下再向左作出一個閉合矩形的手勢.

===================================
12 There -------- outstretched arm, with the index finger pointing to the target.
13 ------ hand held to cover my head, bending elbows, palms cover Tian Linggai.
14 ---- fingers apart to put tear gas was a bowl, covering the nose and mouth of the face.
15. collection -------- wrist for fist-shaped, holding onto the top of the head,
Forefinger erected vertically upwards, slowly making a circle motion.
11.聽到--------舉起手臂,手指間緊閉,拇指和食指觸及耳朵。
12.那裡--------伸開手臂,用食指指向目標。
13.掩護我------把手舉到頭上,彎曲手肘,掌心蓋住天靈蓋。
14.放催淚彈----手指分開呈碗狀,罩住面部的鼻子和嘴巴。
15.集合--------手腕作握拳狀,高舉到頭頂上,
食指垂直向上豎起,緩慢地作圓圈運動。
 ======================================================
======================================================16. advance -------- bent elbow position, forearm pointing to the ground, fingers closed, swinging from behind to the front.
17. understand -------- wrist lifted to the height of the denomination and make a fist-shaped, palm toward those who issued instructions.
18 found sniper - fingers bent, like holding a cylindrical object placed in front, as is generally observed by sniper sight.
19 -------- quickly make a fist state hands, then bend your elbows, lift the arm up and down movement.
20. saw -------- palm slightly bent and pointing players to receive information, fingers closed, palm horizontally on the forehead.
16.推進--------彎曲手肘部位,前臂指向地上,手指緊閉,從身後向前方擺動。
17.明白--------手腕舉到面額高度並作握拳狀,掌心向著髮指令者。
18.發現狙擊手--手指彎曲,像握著圓柱狀物體放在眼前,如同狙擊手通過瞄準鏡進行觀察一般。
19.趕快--------手部作握拳狀態,然後彎曲手肘,舉起手臂作上下運動。
20.看見--------掌心稍微彎曲並指向接受信息的隊員,手指間緊閉,將手掌水平放置在前額上。
 ============================
============================22. ------ closer to my outstretched arm, fingers closed, then swing to his body direction.
23 Directive has received ------ outstretched hand, thumb and forefinger cylindrical shape, with "ok" gesture same.
24. down ----- arms stretched out to the side, elbows bent, palms swinging down to waist height.
25. retreat ------ arm straight down, fist swinging backwards.
21.檢查彈藥------手執一個彈夾,舉到頭頂高度,緩慢地左右擺動.
22.向我靠攏------伸開手臂,手指間緊閉,然後向自己身軀的方向擺動。
23.指令已收到------伸開手,大拇指和食指呈圓形狀,同“ok”的手勢相同。
24.下來-----手臂向身旁伸出,手肘彎曲,掌心向下擺動至腰間高度。
25.撤退------胳膊垂直向下,握拳向後擺動。
 =======================================
=======================================27 single column ------ raised his arm, elbow bent, palms vertical, front and rear for hacking action.
28. double column-shaped ------ elbows bent, hands held to the head, and for the fist-shaped, forefinger and middle finger extended for the hook, back and forth.
29 lateral column ------ hand for a fist-shaped, horizontal laterally extending arm
30.V word formation ------ forearm and body vertically, palm downward swing around.
26.安靜------作握拳手勢,豎起食指,垂直置於唇上。
27.單縱隊------舉起手臂,手肘彎曲,手掌垂直,前後作劈砍動作。
28.雙縱隊形------手肘彎曲,手舉至頭部,並且作握拳狀,食指和中指伸出作鉤狀,前後擺動。
29.橫向縱隊------手部作握拳狀,水平橫向伸出手臂
30.V字隊形------前臂和身體垂直,手掌左右向下擺動。

=====================================================
Graphic sign language used by military reconnaissance squad
軍方偵察小分隊使用的手語圖解
####################################################################
http://www.dailydot.com/crime/chinese-cybercrime-qq-messenger/

The black market for Chinese cybercrime is booming

The Chinese cybercrime underground is bigger and bolder than ever before, according to research from security firm Trend Micro.
Criminal activity has more than doubled in the last year and can be easily found on some of the most popular websites on the entire Internet, the firm, which has been monitoring the country’s illicit circles since 2011, reported.
"The barriers to launching cybercrime have decreased," the report explains. "Toolkits are becoming more available and cheaper; some are even offered free of charge. Prices are lower and features are richer."
The metrics come from several key sources, most notably QQ, a messaging app with 800 million users. QQ boasts over 1.4 million groups related to cybercrime, double the number from the previous year.
Over 100,000 messages about buying and selling malware, text message and email spam, DDoS services, compromised hosts and hacking tools like remote access tools (RATs) are often sent in a single day on QQ alone.


Screenshots via Trend Micro
On average, the cybercrime groups that Trend Micro monitored doubled in size on average from the previous year.
Prices for effective cybercrime tools are downright affordable from a western perspective: A botnet (a network of compromised computers that will do your bidding) of 2,000 slaves costs $596, a trojan to steal bank accounts costs $1,273, and a lifetime DDoS attack kit will run you less than $500.
If you don’t like one seller, worry not. There are over 35,000 compromised hosts on sale, 16,471 DDoS services, and 15,365 RATs.
Perhaps the fastest growing market is mobile hacking, so it’s no surprise that Trend Micro observed tools like SMS servers and SMS spam are in increasing demand.
H/T Infosecurity Magazine | Photo via Hector Garcia (CC BY SA 2.0)
Criminal activity has more than doubled in the last year and can be easily found on some of the most popular websites on the entire Internet, the firm, which has been monitoring the country’s illicit circles since 2011, reported.
"The barriers to launching cybercrime have decreased," the report explains. "Toolkits are becoming more available and cheaper; some are even offered free of charge. Prices are lower and features are richer."
The metrics come from several key sources, most notably QQ, a messaging app with 800 million users. QQ boasts over 1.4 million groups related to cybercrime, double the number from the previous year.
Over 100,000 messages about buying and selling malware, text message and email spam, DDoS services, compromised hosts and hacking tools like remote access tools (RATs) are often sent in a single day on QQ alone.


Screenshots via Trend Micro
On average, the cybercrime groups that Trend Micro monitored doubled in size on average from the previous year.
Prices for effective cybercrime tools are downright affordable from a western perspective: A botnet (a network of compromised computers that will do your bidding) of 2,000 slaves costs $596, a trojan to steal bank accounts costs $1,273, and a lifetime DDoS attack kit will run you less than $500.
If you don’t like one seller, worry not. There are over 35,000 compromised hosts on sale, 16,471 DDoS services, and 15,365 RATs.
Perhaps the fastest growing market is mobile hacking, so it’s no surprise that Trend Micro observed tools like SMS servers and SMS spam are in increasing demand.
H/T Infosecurity Magazine | Photo via Hector Garcia (CC BY SA 2.0)

黑市場,為中國的網絡犯罪正在蓬勃發展
中國的網絡犯罪地下更大,比以往任何時候都更大膽, 據來自安全公司趨勢科技的研究。
犯罪活動增加了一倍多,在過去的一年,可以在一些對整個互聯網上最受歡迎的網站很容易找到,公司,一直在監測該國的非法圈2011年以來,報導。
“的障礙發起網絡犯罪已經減少,”報告說。 “工具包變得更容易獲得和更便宜的,有的甚至是免費提供的價格較低,功能更豐富。”
這些指標來自幾個主要來源,最主要的是QQ的,擁有800萬用戶的消息傳送應用程序。 QQ擁有超過140萬組相關的網絡犯罪,翻一番,從上年同期的數量。
超過10萬對購買和銷售惡意軟件,短信和垃圾郵件,DDoS攻擊服務,受到攻擊的主機和黑客工具,如遠程訪問工具(RAT)的消息往往在一天獨自發在QQ上。


通過趨勢科技截圖
平均而言,網絡犯罪團伙趨勢科技監測的規模擴大了一倍,平均比前一年。
價格有效的網絡犯罪工具是從西方的角度徹頭徹尾的實惠:一個殭屍網絡 (網絡入侵電腦,將做您的出價)2,000奴隸花費$ 596木馬竊取銀行賬戶費用1273美元,並且一生的DDoS攻擊工具包將運行你不到500美元。
如果你不喜歡一個賣方,不擔心。 有超過35,000名受到攻擊的主機上發售,16471 DDoS攻擊服務和15365只。
也許是增長最快的市場是流動的黑客,所以毫無疑問,趨勢科技觀察到類似短信服務器和垃圾短信的工具都在不斷增長的需求。
H / T Infosecurity雜誌 |通過照片赫克托·加西亞 (CC BY SA 2.0)
犯罪活動增加了一倍多,在過去的一年,可以在一些對整個互聯網上最受歡迎的網站很容易找到,公司,一直在監測該國的非法圈2011年以來,報導。
“的障礙發起網絡犯罪已經減少,”報告說。 “工具包變得更容易獲得和更便宜的,有的甚至是免費提供的價格較低,功能更豐富。”
這些指標來自幾個主要來源,最主要的是QQ的,擁有800萬用戶的消息傳送應用程序。 QQ擁有超過140萬組相關的網絡犯罪,翻一番,從上年同期的數量。
超過10萬對購買和銷售惡意軟件,短信和垃圾郵件,DDoS攻擊服務,受到攻擊的主機和黑客工具,如遠程訪問工具(RAT)的消息往往在一天獨自發在QQ上。


通過趨勢科技截圖
平均而言,網絡犯罪團伙趨勢科技監測的規模擴大了一倍,平均比前一年。
價格有效的網絡犯罪工具是從西方的角度徹頭徹尾的實惠:一個殭屍網絡 (網絡入侵電腦,將做您的出價)2,000奴隸花費$ 596木馬竊取銀行賬戶費用1273美元,並且一生的DDoS攻擊工具包將運行你不到500美元。
如果你不喜歡一個賣方,不擔心。 有超過35,000名受到攻擊的主機上發售,16471 DDoS攻擊服務和15365只。
也許是增長最快的市場是流動的黑客,所以毫無疑問,趨勢科技觀察到類似短信服務器和垃圾短信的工具都在不斷增長的需求。
H / T Infosecurity雜誌 |通過照片赫克托·加西亞 (CC BY SA 2.0)
###########################################################
''Una pure disciplinary battalion 'true capacity' exposure was crazy laugh ,,Russian Internet users.
''烏納粹懲戒營'真容'曝光,,遭俄網民瘋狂調侃.
###############################################################
Unidentified Fragments Found in Bodies of MH17 Crew: Dutch Safety Board

Experts working at the Malaysia Airlines Boeing 777 crash site in eastern Ukraine.
© AP Photo/ Dmitry Lovetsky---13:49 10/09/2014---
馬航MH17附近墜毀頓涅茨克
主題: 馬來西亞航空公司波音墜毀在烏克蘭

MH17 Crash Report Beginning of Long Hard Work: Federal Air Transport Agency
Topic: Malaysia Airlines Boeing Crashes in Ukraine
19:19 09/09/2014
MOSCOW, September 9 (RIA Novosti) – The Malaysia Airlines MH17 crash report, published Tuesday by the Dutch Safety Board, is preliminary and marks the beginning of a long hard effort, Oleg Storchevoi, the deputy head of Rosaviatsiya (Russian Federal Air Transport Agency) said Tuesday.
“The report issued is a preliminary document. The investigation of the crash site and the wreckage, its position, should be an important part of this work. It vital to carefully examine all of the radar data, continue its analysis, conduct the autopsies… Without all this information it is impossible to talk about any preliminary conclusions regarding the causes of the crash,” Storchevoi said on Rossiya-24 television channel.
According to him, a lot of time has been wasted.
“Unfortunately, it is impossible not to acknowledge that a lot of time was wasted, and some data will be difficult to analyze. This concerns the study of the remains of the victims, it is also impossible to talk about the complete integrity of the wreckage,” Storchevoi explained.
Flight MH17, flying from Amsterdam to Kuala Lumpur, crashed on July 17 in eastern Ukraine, killing all 298 people on board.
According to the Dutch Safety Board report issued on Tuesday, the plane broke into pieces mid-flight after being hit by “a large number of high-energy objects.”
“The initial results of the investigation point towards an external cause of the MH17 crash. More research will be necessary to determine the cause with greater precision. The Safety Board believes that additional evidence will become available for investigation in the period ahead,” Tjibbe Joustra, Chairman of the Dutch Safety Board said in a press release published on the organization's official website Tuesday.
The experts aim to publish the final report within a year of the date of the crash.
################################################################
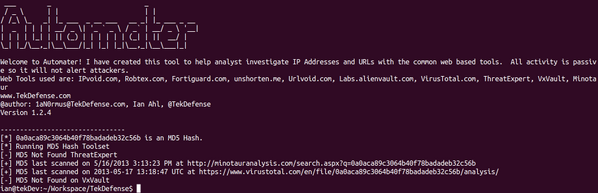
APT challenge memory and malicious software solutions
Comments Posted by Rob Lee 0
APT的內存和惡意軟件解決方案的挑戰
==========
The answer APT memory and malware challenges
APT的內存和惡意軟件的挑戰的答案
Memory image contains launched a real test system APT malware. Your job? Find it.
The purpose of the challenge we face is simple: download the memory image, and trying to answer five questions. Submitted in the contest to succeed, all the answers have to try. Everyone is able to correctly answer three of the five questions will be entered into a drawing to win a free seat DFIRCON Monterey broadcast in March this year. Under normal circumstances, we are very tolerant answer, unless they are completely off base.
If you are interested in learning more about memory analysis, and how it can help you in your research, read all about updates and new FOR526: memory forensics.
Download link memory image: http://dfir.to/APT-MEMORY
Download Link Solution: http://dfir.to/MEMORY-SOLUTION
# Vol.py -f APT.img --profile = WinXPSP3x86 pstree
=========
內存映像包含發動了對測試系統真正的APT惡意軟件。 你的工作嗎? 找到它。
我們面臨的挑戰的目的很簡單:下載內存映像,並試圖回答的5個問題。 要成功提交的較量中,所有的答案必須嘗試。 每個人都能夠正確回答3的5個問題將被輸入到工程圖中贏取免費轉播席位DFIRCON蒙特利今年三月。 一般情況下,我們是非常寬容的答案,除非他們完全關閉基地。
如果您有興趣了解更多關於內存分析,以及它如何幫助你在你的調查,閱讀所有關於更新 和新 FOR526:內存取證。
下載鏈接內存映像: http://dfir.to/APT-MEMORY
下載鏈接解決方案: http://dfir.to/MEMORY-SOLUTION
#vol.py -f APT.img --profile = WinXPSP3x86 pstree

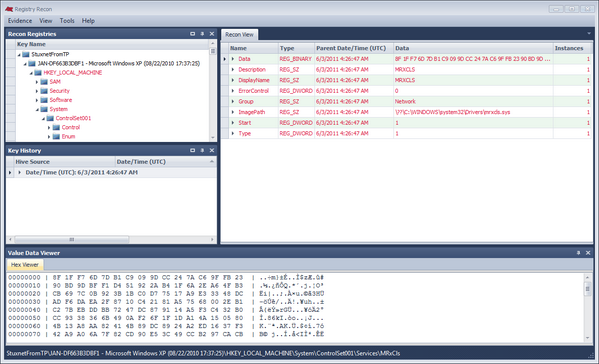
可以從上面看到的iexplore.exe(PID 796)從svchost.exe的(PID 884)衍生。 如果你檢查的波動getsids輸出進行PID 796,你會發現IEXPLORE.EXE運行的系統用戶。 這兩個事件是非常奇怪和不正常的。 IEXPLORE.EXE應explorer.exe的啟動,應該運行的用戶進程。 此外,explorer.exe的也顯示注射了可能毒藤的跡象是通過運行malfind(下面列出的輸出)的觀察。 #vol.py -f APT.img --profile = WinXPSP3x86 connscan

在connscan輸出上面,你注意到的PID 796(IEXPLORE.EXE)被連接到一個遠程系統上的端口89通常是HTTP流量被定向在端口80或443只。 同樣,這將是一個非常奇怪的事情,
見證了一個程序。 這使得iexplore.exe進程十分可疑實在。
#vol.py -f APT.img --profile = WinXPSP3x86 dlllist -p 796

當您檢查dlllist輸出進行PID 796(IEXPLORE.EXE),你會發現有一個流氓命名的DLL,
這是很難看到的。 Irykmmww.d1l被命名為奇,因為DLL被拼寫為1(1)中的第二個字母,
其中一個l(小寫L)應該可以看到。
所以它看起來好像PID 796是惡意軟件,但很明顯,它不能正常啟動。 如果你想看看,如果svchost.exe的注入將失敗,並不會顯示出來。 svchost.exe不噴射。 那麼,如何的惡意軟件開始在系統上?
#vol.py -f APT.img --profile = WinXPSP3x86 svcscan

當我們運行svcscan(服務掃描)插件波動,我們看到的系統,稱為irykmmww這是相同的命名流氓DLL早期發現運行的驅動程序。 為了弄清楚這個驅動是幹什麼的,我們應該檢查驅動程序掛鉤的apihooks和SSDT。
#vol.py -f APT.img --profile = WinXPSP3x86 SSDT | grep的- V NTOSKRNL | grep的- V win32k的

最後,我們可以告訴司機irykmmww.sys是在系統中加載一個rootkit。 顯然,這是為了做文件隱藏等等。
這裡是我們的connscan輸出更早發現IP地址的一些其他信息。
用於218.85.133.23 DNS信息

這是鄧小平同志對惡意軟件的惡意軟件報告。
- 該惡意軟件會創建設備\ Device \ irykmmww(新台幣命名空間)和\\。\ irykmmww(“Win32的”命名空間),並且驅動程序\驅動程序\ irykmmww。 這些都將是正常的工具,如“WINOBJ”看得見的。
- 該惡意軟件可能隱藏一個IEXPLORE.EXE進程中的至少一個實例,例如,它是可檢測的僅與存儲器取證
- 該惡意軟件的內核驅動程序運行的一個名為irykmmww與irykmmww的描述服務。
- 文件,目錄,註冊表項和註冊表值開始的名字irykmmww可能是隱藏的,除非你正在使用的內存取證看看吧
- 該DLL文件irykmmww.d1l(D-1-L)或irykmmww.dll可能出現在處理模塊上市,但文件本身可能仍然隱藏由於rootkit的。
- 該惡意軟件會發出HTTP請求到218.85.133.23 TCP端口89上
- 該惡意軟件可以與URI /index.asp HTTP請求?<編號>,沒有用戶代理
提交的其他分析格布哈特Zocher
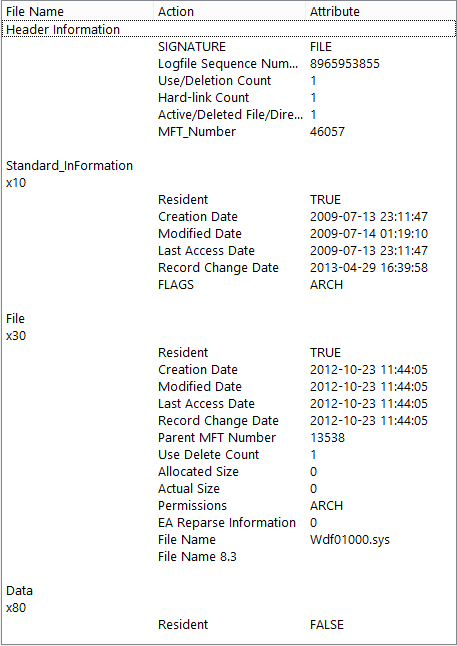
第1階段:識別非法進程 vol.py則PsList:
- 系統啟動時間:2009-04-16 16時10分01秒
- msiexec.exe的(Windows安裝程序,1464,2009-04-16 16:11:02)從開始
服務(704 2009-04-16 16:10:06)
- 從Explorer.exe的(1672,2009-04-16 CMD.EXE(840,2009-05-05 15時56分24秒)
16:10:10)運行MIRAgent.exe(456,2009-05-05十九時28分40秒)
- IEXPLORE.EXE(IE,796,2009-05-05 19:28:28)由svchost.exe的開始
(884,2009-04-16 16:10:07)
vol.py psscan:
- 沒有任何消息
vol.py pstree:
- 沒有任何消息
第二階段:分析過程DLL和把手
vol.py dlllist -p 1464
- 命令行:C:\ WINDOWS \ SYSTEM32 \ msiexec.exe的/ V
- 沒有什麼突出
vol.py dlllist -p 704
- 沒有什麼突出
vol.py dlllist -p 840
- 沒有什麼突出
vol.py dlllist -p 1672
- 沒有什麼突出
vol.py dlllist -p 456
- 好了,命令行顯示這是明顯的MIRA Agend來自Mandiant,
所以對於456一切都不懷疑了
vol.py dlllist -p 796
- 沒有什麼出施坦斯
vol.py dlllist -p 884
- 命令行:C:\ WINDOWS \ SYSTEM32 \ svchost的-k DCOMLAUNCH
所以對於我們仍然有進程:
- msiexec.exe的(Windows安裝程序,1464,2009-04-16 16:11:02)從開始
服務(704 2009-04-16 16:10:06)
- IEXPLORE.EXE(IE,796,2009-05-05 19:28:28)由svchost.exe的開始
(884,2009-04-16 16:10:07)
- >主要是可疑的是,從IE瀏覽器的Svchost啟動884
vol.py getsids -p 796:
揮發性系統波動性框架2.2
IEXPLORE.EXE(796):S-1-5-18(本地系統)
IEXPLORE.EXE(796):S-1-5-32-544(管理員)
IEXPLORE.EXE(796):S-1-1-0(每個人)
IEXPLORE.EXE(796):S-1-5-11(身份驗證的用戶)
- >趣味性,IE瀏覽器作為本地系統運行...
vol.py getsids -p 1464:
揮發性系統波動性框架2.2
msiexec.exe的(1464):S-1-5-18(本地系統)
msiexec.exe的(1464):S-1-5-32-544(管理員)
msiexec.exe的(1464):S-1-1-0(每個人)
msiexec.exe的(1464):S-1-5-11(身份驗證的用戶)
vol.py處理-p 796
! 0x822e9578 796 0x758 0x12019f文件
\設備\ irykmmww
? 0xe10096e0 796 0x7fc 0xf0003 KeyedEvent
CritSecOutOfMemoryEvent
vol.py處理-p 1464
? 0xe10096e0 1464為0x4 0xf0003 KeyedEvent
CritSecOutOfMemoryEvent
! 0x822f2108 1464 0X24 0x1f0001突變
SHIMLIB_LOG_MUTEX
? 0x81e7c8e0 1464 0x100001為0x3C文件
\設備\ KsecDD
? 0x822fe1d0 1464的0x50 0x1f0003事件DINPUTWINMM
? 0x81f07750 1464的0x70 0x12019f文件
在\ Device \ NamedPipe \ NET \ NtControlPipe13
? 0xe1d74160 1464 0xF8的0xf003f重點
MACHINE \ SOFTWARE \ MICROSOFT \ COM3
? 0xe1015030 1464 0x138 0x1f0001港口
OLE6D80DE069215474C95DC80B2A50C
? 0x821607f0 1464 0x1a8 0x120001突變
ShimCacheMutex
? 0xe177e620 1464量0x208 0X2科
ShimSharedMemory
? 0x81da8160 1464 0x274的0x100000事件USERENV:
機器的組策略已經應用
? 0x81f78820 1464 0x278的0x100000事件USERENV:用戶
組策略已經應用
+有關的各種證書密鑰
vol.py filescan
- >不知道的到grep什麼
irykmmww
vol.py svcscan:
- >#1464似乎是合法的,但SHIMLIB_LOG_MUTEX可疑
- >可能插入?
可疑的進程:
偏移:0x38ab98
訂單:252
進程ID: -
服務名稱:irykmmww
顯示名稱:irykmmww
服務類型:SERVICE_KERNEL_DRIVER
服務狀態:SERVICE_RUNNING
二進制路徑:\驅動程序\ irykmmww
vol.py filescan | grep的-i irykmmww
揮發性系統波動性框架2.2
0x01f1cd20 1 0 -W ----
在\ Device \ HarddiskVolume1 ???? UME〜1 \演示\ LOCALS〜1 \ TEMP \ irykmmww.log
0x01f20d20 1 0 R - 路
在\ Device \ HarddiskVolume1 \ WINDOWS \ SYSTEM32 \ DRIVERS \ irykmmww.sys
0x02121e08 1 0 R - 路
在\ Device \ HarddiskVolume1 \ WINDOWS \ SYSTEM32 \ irykmmww.dll
0x02387908 1 0 R -----
在\ Device \ HarddiskVolume1 \ WINDOWS \ SYSTEM32 \ irykmmww.d1l
0x023beca8 1 0 R - 路
在\ Device \ HarddiskVolume1 \ WINDOWS \ SYSTEM32 \ irykmmww.d1l
0x02f7cd20 1 0 R - 路
在\ Device \ HarddiskVolume1 \ WINDOWS \ SYSTEM32 \ DRIVERS \ irykmmww.sys
0x03282e08 1 0 R - 路
在\ Device \ HarddiskVolume1 \ WINDOWS \ SYSTEM32 \ irykmmww.dll
0x1347fd20 1 0 R - 路
在\ Device \ HarddiskVolume1 \ WINDOWS \ SYSTEM32 \ DRIVERS \ irykmmww.sys
總結:
- IE瀏覽器從796 SVCHOST跑
- 可疑的MS安裝過程1464
- 可疑服務的W / O進程ID
- 可疑文件:
???? UME〜1 \演示\ LOCALS〜1 \ TEMP \ irykmmww.log
\ WINDOWS \ SYSTEM32 \ DRIVERS \ irykmmww.sys
\ WINDOWS \ SYSTEM32 \ irykmmww.dll
第三階段:檢查網絡文物
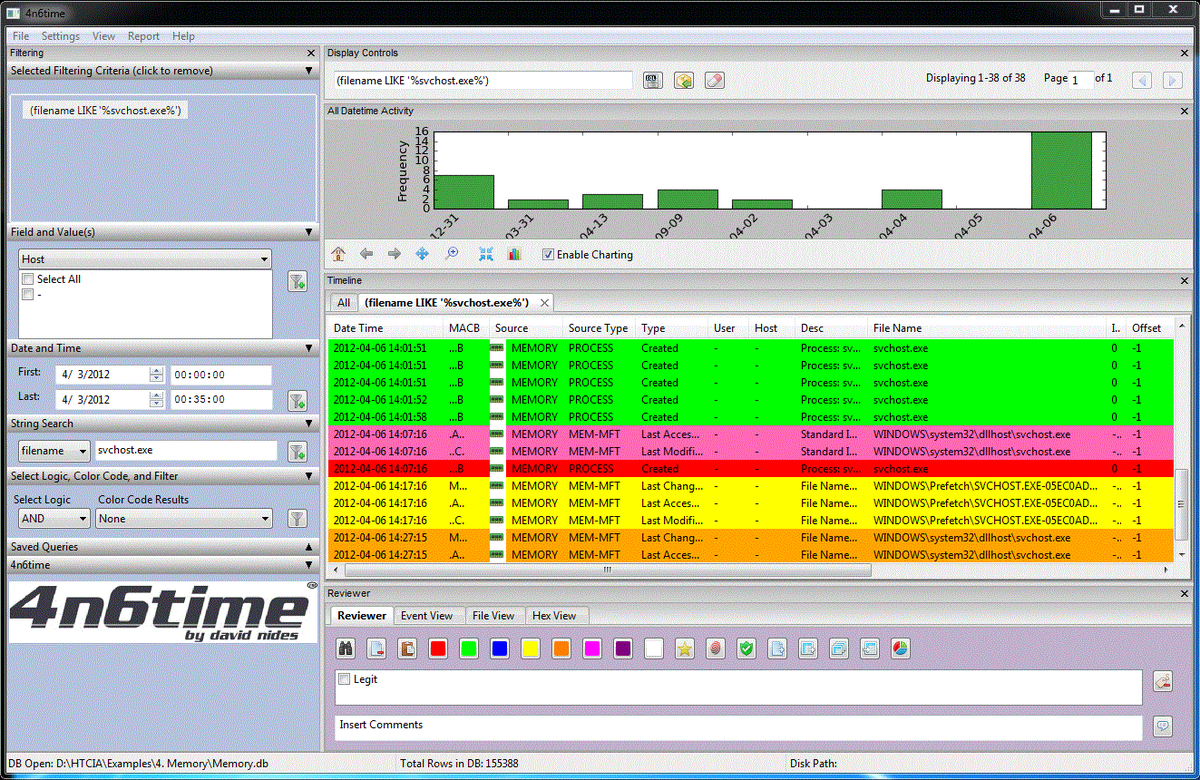
vol.py連接
0x81e611f8 192.168.157.10:1053 218.85.133.23:89 796
- > IE瀏覽器上的端口89訪問系統在中國
inetnum:218.85.0.0 - 218.86.127.255
網絡名:CHINANET-FJ
DESCR:CHINANET福建省網絡
DESCR:數據通信事業部
DESCR:中國電信
國家:中國
vol.py connscan
此外:
192.168.157.10:1050 222.128.1.2:443 1672
- > Explorer.exe的已經在中國HTTPS訪問網站
inetnum:222.128.0.0 - 222.131.255.255
網絡名:聯通,北京
DESCR:中國聯通北京地區網絡
DESCR:中國聯通
國家:中國
被關閉的連接,所以應前happend
vol.py插座:
0x822ef510 796 1053 6 TCP 0.0.0.0 2009-05-05
19時29分06秒
0x822d25b0 4 0 47 GRE 0.0.0.0 2009-05-05
19時28分35秒
0x822f6618 4 1052 6 TCP 0.0.0.0 2009-05-05
19時28分35秒
- > IE瀏覽器監聽端口1053 ...
vol.py sockscan
- 什麼新鮮事
第4階段:查找代碼注入的證據
vol.py malfind --dump-DIR ./outdir/> malfind.out
有趣的作品:
過程:explorer.exe的PID:1672地址:0x2570000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x1820000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x1680000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x1670000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x16a0000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x1690000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x16b0000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x16c0000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x16d0000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x16e0000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x16f0000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:explorer.exe的PID:1672地址:0x1810000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:1,MemCommit:1,PrivateMemory:1,防護等級:6
過程:msiexec.exe的PID:1464地址:0x12f0000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:3,PrivateMemory:1,防護等級:6
過程:msiexec.exe的PID:1464地址:0x1350000
VAD標籤:威斯保護:PAGE_EXECUTE_READWRITE
標誌:CommitCharge:3,PrivateMemory:1,防護等級:6
vol.py ldrmodules -p 1672
1672 Explorer.exe的0x00970000真真真
\ WINDOWS \ SYSTEM32 \ irykmmww.dll
vol.py ldrmodules -p 1464
- 沒有什麼突出
階段5:檢查一個rootkit的跡象
vol.py psxview
- 沒有什麼突出
vol.py MODSCAN
0x01f1c7d0 irykmmww.sys 0xf836f000為0x4000
\?\ C:\ WINDOWS \ SYSTEM32 \ DRIVERS \ irykmmww.sys
vol.py apihooks -p 1672 -Q
- 什麼
vol.py apihooks -p 1464 -Q
- 什麼
vol.py SSDT | egrep的-v“(NTOSKRNL | win32k的)'
揮發性系統波動性框架2.2
[86]收集所有引用SSDTs從KTHREADs ...
尋找合適的地址空間表...
SSDT [0]在80501b9c有284項
報名0x0042:0xf836fe9c(NtDeviceIoControlFile)由irykmmww.sys資
報名0x0047:0xf83706dc(NtEnumerateKey)由irykmmww.sys資
報名0x0049:0xf837075e(NtEnumerateValueKey)由irykmmww.sys資
報名0x0077:0xf837028f(NtOpenKey)由irykmmww.sys資
報名0x0091:0xf8370a8c(NtQueryDirectoryFile)由irykmmww.sys資
進入0x00ad:0xf836fe3e(NtQuerySystemInformation)所擁有的
irykmmww.sys
進入0x00b1:0xf837091a(NtQueryValueKey)由irykmmww.sys資
SSDT [1]在bf999d00 667項
vol.py driverirp -r TCPIP
- 沒有什麼突出
vol.py IDT
- 沒有什麼突出
第六階段:自卸可疑進程和驅動程序
vol.py dlldump --dump-DIR ./outdir -p 1672 -r irykmmww
揮發性系統波動性框架2.2
過程(五)名稱模塊基本模塊名稱結果
---------- -------------------- ----------- --------- -----------------
0x81da71a8的explorer.exe 0x000970000 irykmmww.dll確定:
module.1672.1fa71a8.970000.dll
MD5SUM OUTDIR / module.1672.1fa71a8.970000.dll
319bff282b3046e6c85bbe0e67338c72 OUTDIR / module.1672.1fa71a8.970000.dll
- >
https://www.virustotal.com/en/file/fe9fbcc2cf6c6666d2cdd17b7665ce66fd3ba2ceec381cf4ea09f2a7a3387749/analysis/
vol.py moddump --dump-DIR ./outdir -r irykmmww
揮發性系統波動性框架2.2
模塊基本模塊名稱結果
----------- -------------------- ------
0x0f836f000 irykmmww.sys確定:driver.f836f000.sys
MD5SUM OUTDIR / driver.f836f000.sys
c8c2e11f5627f9f143152aec4e61c10b OUTDIR / driver.f836f
- >
https://www.virustotal.com/en/file/a80d0353c34c20a50a35771e3794de255e9030d8b7ab21ef6d1953afa692dd97/analysis/
總結:
- 系統感染了內核驅動irykmmww.sys
(\ WINDOWS \ SYSTEM32 \ DRIVERS \ irykmmww.sys,c8c2e11f5627f9f143152aec4e61c10b)
它負載在啟動時
- explorer.exe的(1672)感染irykmmww.dll
(\ WINDOWS \ SYSTEM32 \ irykmmww.dll,319bff282b3046e6c85bbe0e67338c72
- 讓每一個用戶進程是在攻擊者的控制權
- explorer.exe的(1672)通過HTTPS訪問的網站在中國
192.168.157.10:1050 222.128.1.2:443
- IE瀏覽器(796)上的端口89訪問系統在中國:
192.168.157.10:1053 218.85.133.23:89
- 日誌文件可能包含更多信息:
???? UME〜1 \演示\ LOCALS〜1 \ TEMP \ irykmmww.log
###########################

#########################################################

Friday, September 5, 2014
Super Sunday Funday Forensic Challenge
Hello Reader,
It's time for another multi week, multi stage challenge! Get ready!
Read about it from the SANS Blog here:
http://dfir.to/HECF-Challenge-14
https://mega.co.nz/#!qoxgGYCY!1jM32pncF0wE-TROhaXFI07hZbu5AfZ1BJE-p8tm1mo
and email the answer to the following questions
I decided to go ahead and crank up the difficulty on this challenge from the get go and my goal is to have all 5 levels by forensic image reviews. Good luck to all of you!
On receiving a correct answer you will be notified that you have entered stage 2 and that another question and image will be sent to you. There are 5 stages and the player who makes it the farthest with the most correct answer will win!
The Rules, Have Changed!:
1. This will be a multi stage contest lasting two weeks
2. Final answers must be in by Sept 15th
3. 9/05/14 The first question will be posted
4. New questions will be given to those who answer the first question correctly
5. You can start the contest at any point leading up to Sept 15th,there is no penalty for starting late
6. All submissions must be sent to dcowen@g-cpartners.com, do not post answers in the comments
7. In order for an anonymous winner to receive a prize they must give their name to me, but i will not release it in a blog post
FOR408: Windows Forensic Analysis
Oct 6, 2014 - Nov 12, 2014
w/ Mike Pilkington & Ovie Carroll
FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques
Oct 13, 2014 - Nov 19, 2014
w/ Lenny Zeltser & Jake Williams
FOR508: Advanced Incident Response
Oct 14, 2014 - Nov 20, 2014
w/ Jake Williams & Alissa Torres
It's time for another multi week, multi stage challenge! Get ready!
Read about it from the SANS Blog here:
http://dfir.to/HECF-Challenge-14
The Challenge:
The first forensic image is available for download. Your goal is to solve the question with the first forensic image located at:https://mega.co.nz/#!qoxgGYCY!1jM32pncF0wE-TROhaXFI07hZbu5AfZ1BJE-p8tm1mo
and email the answer to the following questions
- What was used to wipe this drive?
- What special options were given?
- What file was wiped from this drive?
I decided to go ahead and crank up the difficulty on this challenge from the get go and my goal is to have all 5 levels by forensic image reviews. Good luck to all of you!
On receiving a correct answer you will be notified that you have entered stage 2 and that another question and image will be sent to you. There are 5 stages and the player who makes it the farthest with the most correct answer will win!
The Rules, Have Changed!:
1. This will be a multi stage contest lasting two weeks
2. Final answers must be in by Sept 15th
3. 9/05/14 The first question will be posted
4. New questions will be given to those who answer the first question correctly
5. You can start the contest at any point leading up to Sept 15th,there is no penalty for starting late
6. All submissions must be sent to dcowen@g-cpartners.com, do not post answers in the comments
7. In order for an anonymous winner to receive a prize they must give their name to me, but i will not release it in a blog post
The Prize:
A free vLive DFIR Online LIVE Course from SANS a prize worth $5,000, you can choose from the following:FOR408: Windows Forensic Analysis
Oct 6, 2014 - Nov 12, 2014
w/ Mike Pilkington & Ovie Carroll
FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques
Oct 13, 2014 - Nov 19, 2014
w/ Lenny Zeltser & Jake Williams
FOR508: Advanced Incident Response
Oct 14, 2014 - Nov 20, 2014
w/ Jake Williams & Alissa Torres
============
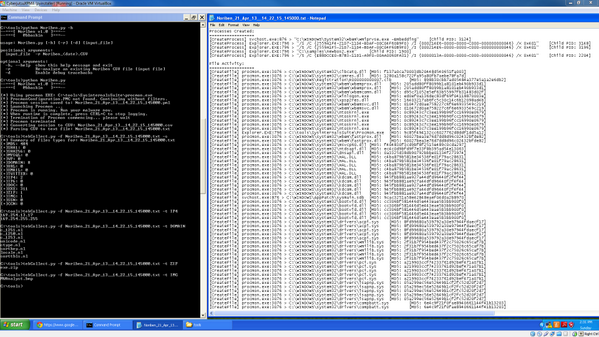
週二,2014年8月5日
三角力量在黑帽阿森納
您好讀卡器,
這是一個位,我知道,我很喜歡我的博客短暫的休息時間而有大量的工作正好! 我今天的標題為入侵者,我很高興地說,我將在黑帽阿森納在週三14年8月6日表示,從上午10時至上午12時30分三角力量ANJP商業版。 如果你打算在那裡,我希望你來打招呼,如果沒有別的。 我們正在努力了很多新的功能,我將演示該如:
想知道更多嗎? 點擊此處查看我們為阿森納房源: https://www.blackhat.com/us-14/arsenal.html#Cowen
點擊這裡了解更多關於三角力量ANJP: https://www.gettriforce.com/product/triforce-anjp/
這是一個位,我知道,我很喜歡我的博客短暫的休息時間而有大量的工作正好! 我今天的標題為入侵者,我很高興地說,我將在黑帽阿森納在週三14年8月6日表示,從上午10時至上午12時30分三角力量ANJP商業版。 如果你打算在那裡,我希望你來打招呼,如果沒有別的。 我們正在努力了很多新的功能,我將演示該如:
- 支持雕花USN日誌條目
- 支持圖像取證
- 支持的期刊超過400GB大小
- 更快的處理
- 更多的簽名!
想知道更多嗎? 點擊此處查看我們為阿森納房源: https://www.blackhat.com/us-14/arsenal.html#Cowen
點擊這裡了解更多關於三角力量ANJP: https://www.gettriforce.com/product/triforce-anjp/

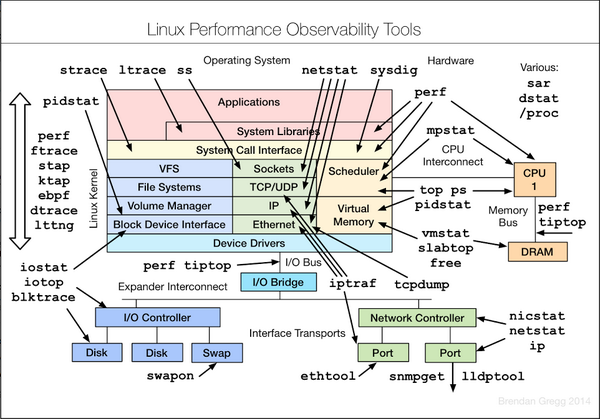
#dfir 的搜尋結果
格線 /
列表


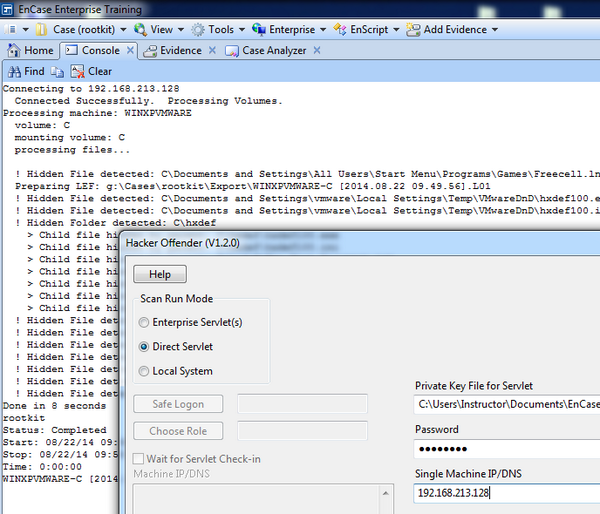







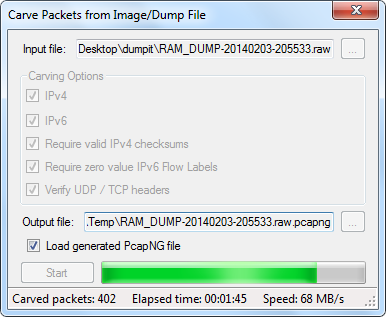
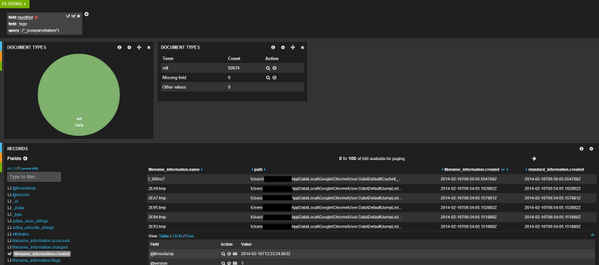


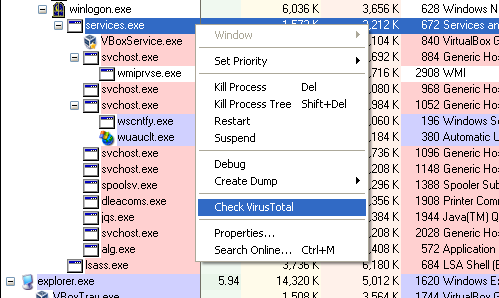










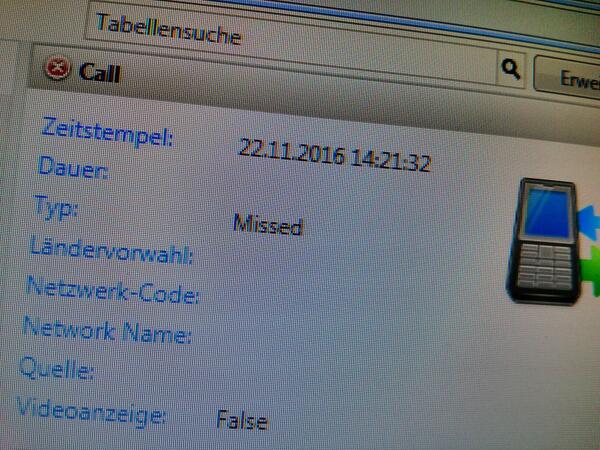





################################################################
"Do my best .... uncover layer after layer of false
My co-responsibility for the little people
Do you want to make brow furrowed ...
I would also like to thank a hidden '' You 'for me to navigate
On the network this matter, simply can not afford, and that you * so I did it, the pro ~ ~ ~ "
http://melodytoyssexy.blogspot.com/2014/09/to-my-favorite-president-obama-and.html
"盡我所能....揭開一層又一層的虛假
我的共同為人們的小責任
希望能讓你們眉頭不要深鎖...
我也要謝謝一個隱藏著的''你''為我導航
在網絡上這事,根本負擔不來,這個你*令我辦到了,親~~~"
http://melodytoyssexy.blogspot.com/2014/09/to-my-favorite-president-obama-and.html
---**To my favorite "President Obama" and the defense team of people, these sins, you see ... ** !!!
---**給我最愛的"奧巴馬總統"及防衞人們的隊伍,這些罪惡,你們看...**!!!
**USA/UK/TW/MACAU(FDZ)/KOREN/FR/UKN/PH/POLA/........All the world city lauguage**-
===MelodyRO===THE END===>/
&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
1.jpg)






































1.jpg)


