 *---By*tribal*Chief Information Security Officer **Pierluigi Paganini**disclose share-*China Comment crew into taking over fake water "- and *accused of cyber espionage against U.S. companies five Chinese People's Liberation Army officials *-
*---By*tribal*Chief Information Security Officer **Pierluigi Paganini**disclose share-*China Comment crew into taking over fake water "- and *accused of cyber espionage against U.S. companies five Chinese People's Liberation Army officials *----由*首席信息安全官部落*皮耶路易吉帕格尼尼*透露分享--*中國評論船員陷入接管假水廠"--和*被指網絡間諜對美國公司5名中國解放軍官員*-
---*부족*최고 정보 보안 책임자 Pierluigi 파가니니*이 주 공개함으로써- "가짜 물 위에 복용으로*중국 주석 승무원 -그리고*미국에 대한 사이버 스파이 혐의로 기소 회사 오 중국 인민 해방군 관리*-
**USA/UK/TW/MACAU(FDZ)/KOREN/......all the world city lauguage**
*
**--Please use Google with a
large family of God translator to translate your country / language city Oh ^ ^
--請各位用家善用谷歌大神的翻譯器,來翻譯你們的國家/城市的語言喔^^
--Por favor, use o Google com
uma grande familia de Deus tradutor para traduzir sua cidade pais / idioma Oh ^
^
--** - 국가 / 언어 시 를 번역하는 하나님 번역기 의 큰 가족과 함께 구글을 사용하십시오 아 ^ ^
--S'il vous plait utilisez
Google avec une grande famille de Dieu traducteur pour traduire votre ville de
pays / langue Oh ^ ^
--Bitte verwenden Sie Google
mit einer grosen Familie Gottes Ubersetzer zu Ihrem Land / Sprache ubersetzen
Stadt Oh ^ ^
--*** - あなたの国/言語の街を翻訳する神トランスレータの大きなファミリーでGoogleを使用してくださいああ^ ^
** - Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--** - Utilice Google con una
gran familia de Dios traductor para traducir tu ciudad país / idioma Oh ^ ^
** - Si prega di utilizzare
Google con una grande famiglia di Dio traduttore per tradurre la tua città paese / lingua Oh ^ ^
--Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--Bonvole uzu Google kun
granda familio de Dio tradukisto traduki via lando / lingvo urbon Ho ^ ^
http://translate.googleusercontent.com/translate_c?depth=2&hl=zh-CN&rurl=translate.google.com&sandbox=0&sl=auto&tl=zh-TW&u=
http://securityaffairs.co/wordpress/16961/hacking/chinese-comment-crew-caught-taking-over-a-fake-water-plant.html&usg=ALkJrhjKjrjIv2zOi9-PxuXYhWXlqybeSw
In the August 7, 2013 === * China Comment crew into taking over fake waterworks "Chinese hackers take over the team reviews the crew into a honeypot simulated water,Chinese PLA network element unlimited offensive.
The hacker group attacked the crew comment irrigation facilities counterfeit U.S. control system has been identified.
Researchers deploy a honeypot to collect, causing a chain of links to popular hacker group attacked annotation crew also Mandiant intelligence firm evidence described APT1.
 According to data from the security firm's collective views of the crew is directly related to the Chinese People's Liberation Army troops provided a network.
According to data from the security firm's collective views of the crew is directly related to the Chinese People's Liberation Army troops provided a network.News about the operation has been 凯尔韦赫特, researchers at Trend Micro released
During the last Black Hat conference.
Chinese hackers are considered the most insidious persistent collectors U.S. intelligence
They are also a serious threat to many critical infrastructure in the United States.
Many studies have found that fragile and damage control systems of these high-risk network infrastructure attacks, it is not the first time, the attacker to locate a water control, the control system was hit last December, the United States municipality, but fortunately this is a decoy set up by Kyle Wilhoit Word document using hidden malware full access. Development framework browser Wilhoit used by hackers to gain access to a system, the establishment of high-precision position, also thanks to the data of their WiFi card.
 Security experts analyzed the attackers and their data search and noted that hackers have targeted categories, they played a profound understanding of the behavior.
Security experts analyzed the attackers and their data search and noted that hackers have targeted categories, they played a profound understanding of the behavior."You would think he has to say about the crew will not come after the local water authority," "In fact, I watched the attack interface of the machine, which is 100% clear that they know what they're doing." Revealed Wilhoit.
Honeypot is usually part of a real device or network, accurate copy, they are used to detect, mitigate or offset attempt cyber attacks, for which it is usually isolated and oversight owners. In the specific case of honeypots reproduction of the Internet interface, various important infrastructure for the ICS / SCADA system deployment, such as electricity and water supply facilities.
The researchers created a plant thanks to cloud computing fake network,
Such attackers believe that the system is located in the world, including Australia, Brazil, Ireland,
Russia, Singapore, and of course the various components of the United States.
*Pierluigi Paganini*

===========================================
http://securityaffairs.co/wordpress/25070/cyber-crime/pla-officials-accused-hacking.html&usg=ALkJrhjqclhQ6zsH4HDZj3zvEjuVPMdchg
- Accused of cyber espionage against U.S. companies five Chinese People's Liberation Army officers -
--- By Pierluigi Paganini on May 20, 2014

The United States has filed criminal charges against five Chinese People's Liberation Army military officials network of spies and hackers on several American companies.
Earlier this week, the United States charged five Chinese People's Liberation Army military officers and accused them invade American computer company. U.S. authorities accused the American invasion of China's People's Liberation Army officer in the energy sector theft of trade secrets and intellectual property.
United States Department of Justice has issued a press release, which said the time period of five hackers and cyber attacks victim companies, following an abstract name from the indictment:

Defendant: Wang Dong, SUN Kai Liang, Wen Xinyu Huang Zhenyu and 顾春晖, who was third at 61,398 units in the Chinese People's Liberation Army officer's (PLA) is. The indictment said Wang, Sun, and Wen Jiabao, and other known and unknown to the grand jury, hacker attacks or attempts to invade named in the indictment, and yellow, Gu support their conspiracy, among other things, infrastructure management United States entity (such as a domain account), for hacker attacks.
Victims: Westinghouse Electric Company (Westinghouse), Solar World Company (SolarWorld company), United States Steel Corporation (U.S. Steel), Allegheny Technologies (ATI), United States Steel, Paper and Forestry, Rubber, Manufacturing, Energy U.S. subsidiaries, related industrial and service personnel international Union (USW) and Alcoa
Time period: 2006-2014.
FBI accused of hacking and total application PLO official count of 31 charges, as follows:
Conspiracy to commit computer fraud and abuse
Access (or attempt to access), a protected computer without authorization to obtain the purpose of commercial interests and personal economic interests of information,
Sending program, information, code or command, with intent to cause damage to a protected computer
Aggravated identity theft
Economic espionage
Trade secret theft
"When a foreign country to use military or intelligence resources and tools,
American executives or company to obtain trade secrets or sensitive commercial information,
The interests of its state-owned enterprises,
We must say, 'Enough,' "United States Attorney General Eric Holder announced at a news conference.
Accompanying the indictment states:
Up to and including "From at least in or about 2006, at least in our April 2014,
The members of the People's Liberation Army ("PLA"), the People's Republic of China Army ("China"),
United States of conspiracy and computer and other business entities invaded Western Pennsylvania and elsewhere. "
The Chinese government denied the allegations, saying that the incident would damage relations between the two countries.
Cyber espionage is the highest national security concerns between the two governments,
T op American intelligence officials announced in early 2014 a new global threat assessment report at a Senate hearing, the document takes into account the impact of the foreign network activity state-backed hackers,
As pose a serious threat to homeland security.
US Intelligence Security Affairs Worldwide Threat Assessment Report 13-14 PLA
U.S. authorities suspected hackers work unit 61398 PLA headquarters in Shanghai,
According to the survey, hackers have stolen trade secrets,
Also related to the cost of nuclear power plant design and solar panels company's sensitive data and price data.
Federal prosecutors suspect that the target company's list is very long,
Including Alcoa, Allegheny Technologies, Inc., United States Steel Corporation,
Toshiba unit Westinghouse Electric Company, the company's U.S. subsidiary, Solar World,
Steelworkers union and the loss of American officials in accordance with the company is "significant."
"The victim had filed against their Chinese competitors an unfair trade all claims,
Help Washington to draw the so-called hacker activities and their impact on international business links between.
"Reuters reported.
Five PLO çhinese officials were U.S. authorities, international fugitives believed,
The indictment is a clear message to other governments,
United States does not want to accept the company further cyber espionage, curious,
If we consider a file-based Snowden recently disclosed cyber espionage against the United States abroad.

---Please note that the report of the text in the indictment, "the indictment is merely accused, the defendant is presumed innocent unless proven guilty in court." @
===================
Chinese leaders will try to focus on domestic priorities in 2014, while taking advantage of China's
Growing influence in the region. Xi is a new generation of leadership in place, its ambitious policy
Agenda into the focus: to accelerate economic reforms, to make management more efficient,
Responsible, and tighten the Communist Party discipline.
China will likely continue its more positive attitude, maritime disputes, including tough
Position on the Senkaku Islands in Japan. More broadly, China's growing confidence in the new
Capabilities, and other cognitive challenges China's interests and security will push Beijing to pursue
A more active foreign policy.
More and more territorial disputes between competing regional competition and an increased risk of nationalist sentiment
Upgrade and constraints of regional cooperation. Sovereignty and historical resurrection
Resentment generated friction between East and 华南申 claimant and occasional events
China Ocean slow or stall bilateral or multilateral efforts to resolve the dispute.
Beijing highlights its pursuit of "new relations between big powers" in Washington, but China is
While working at least indirectly balance American influence. In East Asia, Beijing
================================================== 單位61398
http://translate.googleusercontent.com/translate_c?depth=2&hl=zh-CN&rurl=translate.google.com&sandbox=0&sl=auto&tl=zh-TW&u=http://securityaffairs.co/wordpress/12452/intelligence/mandiant-report-on-apt1-chinas-cyber-espionage-units.html&usg=ALkJrhgp46Z-2kEOc2ZyDlCUFYCuzPnOUw
APT1 with China on cyber espionage forces Mandiant report

Earlier this month, someone spread the news about a complex cyber espionage dollar against major media organizations in the movement, including the New York Times and Washington Post, hackers trying to destroy the reporter's e-mail accounts, steal sensitive information. The campaign appeared very aggressive, hackers had tried to infiltrate the network using 45 instances of journals targeted malware forensic analysis revealed by Mandiant security company.
Mandiant experts pointed out that the hackers began to work, in most cases, at 8:00 GMT operate a standard working day, but the Group of hackers also attacked regularly stopped for a few weeks.
The New York Times reported that:
"Hackers trying to penetrate the American University in computer and, through their routing attacks, the source of the attack cloak a hundred times, said in a Mandiant, was the era of the company hired a computer security expert. This has been traced to China in Mandiant many other attack used subterfuge. "
After a few weeks Mandiant® Intelligence Center ™ released shocking report reveals an enterprise-level computer espionage is called APT1. APT1 is known as one of the many terms cyber espionage a major amount of the stolen information around the world.
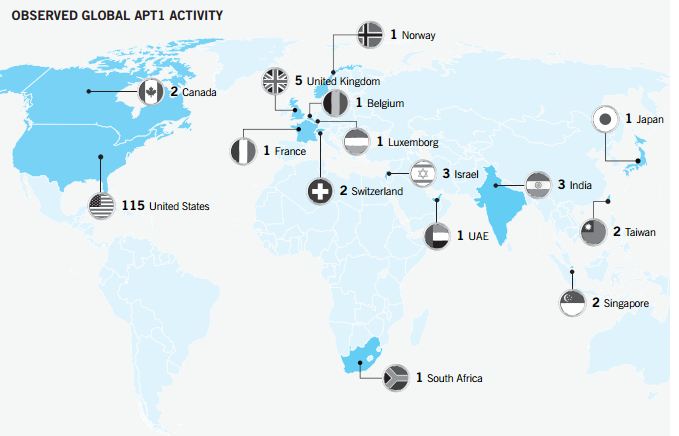
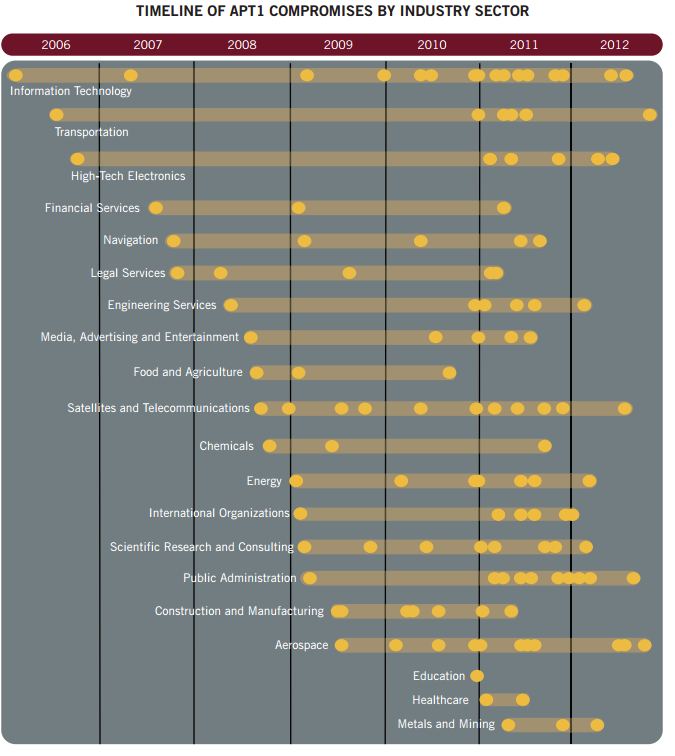
Contact by evidence gathered together security experts APT1 to People's Liberation Army (PLA) General Staff (GSD) Part 3 (Military Cover Code 61398), China's second game, but what is really impressive is that the action distant started in 2006 for multiple industries 141 victims.
Here are the famous "unit 61398 Information:
On the nature of the work "units 61,398's" is considered a state secret in China; however, we believe in the harmful "computer network operations."
Unit 61398 section is located in Datong Road (Datong Road) in Gaoqiao Town (Gaoqiao), which is located in Pudong New Area of Shanghai (Pudong New Area) (Shanghai). This compound in the center of the building is a 130,663 square feet facility is 12 storeys high, was built in early 2007.
We estimate that 61,398 shares by hundreds of staff, perhaps thousands of people on the basis of the size of the unit 61398 of physical infrastructure.
Dedicated fiber optic communications infrastructure equipment in the name of defense of China Telecom to offer.
61,398 requests for its staff in computer security and computer network operations training, also requires its staff to be proficient in English.
Mandiant identified APT1 activities to the four major networks in Shanghai, where two of the Pudong New Area, the basis of which 61,398 shares.
In attackers to take over APT1 malware families, and revealed that the report APT1 way (tools, strategies, programs), including the compilation of the video shows the actual APT1 activities.
The Mandiant also identified more than 3000 indicators to improve the defense of APT1 action, and release of a specific document, will address these issues, including APT1 indicators, such as domain names, MD5 hash value of the IP address and malicious software.
APT1 systematically steal victims' organizations hundreds of TB of data, and has demonstrated the ability and intent to steal from dozens of organizations at the same time.
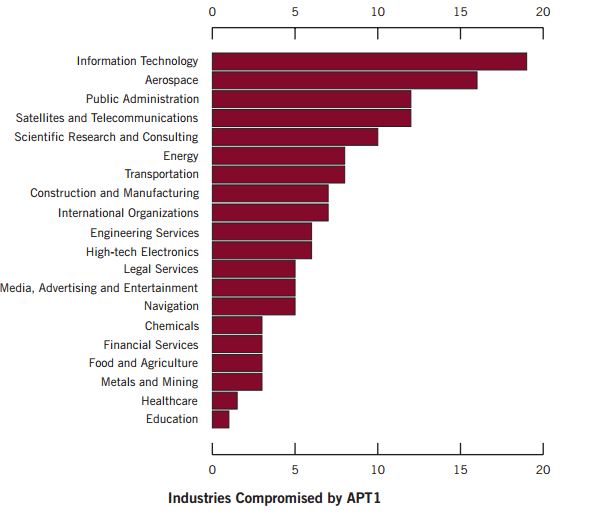
--APT1 Is a continuous collector, once APT1 established a visit, they regularly visit the victim's network to steal a very long time-sensitive information and intellectual property, usually remain in contact with the victim's network, with an average 356 days.
The longest period of time APT1 maintain network access of victims is 1764 days, four years and ten months.
In the precious document Mandiant also recommended:
Use APT1 thirteen (13) X.509 certificate encryption.
A compromise APT1 indicators (international oil companies) and 40 series of numbers malware arsenal of weapons APT1 detailed description exceeded.
IOC can be used in conjunction with Red ™, freedom Mandiant host-based survey tool, or with Mandiant Intelligent Response® (MIR), Mandiant commercial enterprise survey tool.
Mandiant manager has decided to make an exception to its traditional policy of non-disclosure, as it relates to risk majestic cyber espionage and its impact on the global economy, the victim of offensive to many countries and related industries.
Following Paul's an interesting statement:
"Now is the time to recognize the threat from China, and we hope to do our part to arm and prepare security professionals to effectively combat the threat. Ownership issue has been APT's cyber espionage on the landscape of public understanding of a missing link. If not established to establish strong links with China, there is always space for observers to dismiss the Asia-Pacific operations of uncoordinated individual criminal in nature, or peripheral larger national security and global economic concerns and we hope that this report will lead to more APT understand and respond to network breaches concerted action. "
Cyber war has started a long time ago!
Pierluigi Paganini
lnkd.in/dEdab95
########################################
http://melodytoyssexy.blogspot.com/2014/09/bytribalchief-information-security.html
============================================================

http://translate.googleusercontent.com/translate_c?depth=2&hl=zh-CN&rurl=translate.google.com&sandbox=0&sl=auto&tl=zh-TW&u=http://securityaffairs.co/wordpress/25070/cyber-crime/pla-officials-accused-hacking.html&usg=ALkJrhjqclhQ6zsH4HDZj3zvEjuVPMdchg
中國評論船員陷入接管假水廠

中國黑客團隊評論船員陷入接管一個蜜罐模擬水廠,與解放軍中國網絡單元的無限攻勢。
該評論船員黑客集團的攻擊的水利設施假冒美國的控制系統中得到確定。 研究人員部署一個蜜罐來收集,導致鏈接鏈到黑客的流行組註釋船員也被Mandiant情報公司所描述的攻擊證據 APT1 。據由安全公司的集體意見船員直接關係到中國解放軍的網絡部隊提供的數據。
有關操作的消息已經被凱爾韋赫特,研究人員在趨勢科技發布的,最後黑帽大會期間。
中國黑客被認為是最陰險的執著收藏家的美國情報,他們是一個嚴重的威脅也是美國境內的許多關鍵基礎設施。
許多研究發現,這些基礎設施的脆弱與破壞的高風險網絡攻擊的控制系統,它不是第一次,攻擊者定位一個控水,去年十二月被打控制系統為美國的直轄市,幸好這是一個誘餌成立由Kyle韋赫特使用Word文檔隱藏惡意軟件的完全訪問。 韋赫特使用的瀏覽器的開發框架 ,以獲得進入黑客的體制,建立高精度的位置,也多虧了他們的WiFi卡的數據。
安全專家分析了攻擊者和他們的數據搜索並指出,黑客有目標的類別,他們打了一個深刻的認識的行為。
“你會覺得他有什麼看法船員不會來當地水務局後,” “其實,我觀看了本機的攻擊界面。 這是100%的清楚,他們知道他們在做什麼 。“透露韋赫特。蜜罐通常是真正的設備或網絡的一部分,精確的複製,它們被用來偵測,減輕或抵消嘗試網絡攻擊,為此它通常是孤立和監督業主。 在具體情況下的蜜罐再現了互聯網接口,為ICS / SCADA系統部署的各項重要的基礎設施,如電力和供水設施。
研究人員創建了植物的感謝雲計算的假網絡,這樣攻擊者相信,該系統被設在全球包括澳大利亞,巴西,中國,愛爾蘭,俄羅斯,新加坡, 當然還有美國的各個組成部分。
從三月到2013年6月韋赫特計入了12 蜜罐近74網絡攻擊,其中超過50%是來自中國,德國,英國,法國,巴勒斯坦和日本。 十大襲擊造成高精密,並根據安全專家,他們能夠摧毀蜜罐的控制系統。
結果是非常令人擔憂的,他們是證明了贊評論乘員組在中央政府的控制下工作,並增加針對關鍵基礎設施外國的。
“74攻擊蜜罐來自16個不同國家。 大部分非關鍵的攻擊,67%,起源於俄羅斯,以及少數來自美國大約有一半的關鍵攻擊起源於中國,其餘來自德國,英國,法國,巴勒斯坦和日本。 結果導致韋赫特得出結論,自來水廠,並有可能等設施,在世界各地都被成功地破壞和外部攻擊者所採取的控制,即使沒有大的攻擊已經上演。 “這些攻擊正在發生和工程師們可能不知道,”他告訴麻省理工學院技術評論 。世界上許多其它控制系統可能已經受損嚴重的後果,中國被認為是幾乎全部的國家的網絡攻擊的主要來源。
皮耶路易吉帕格尼尼
( 安全事務 -網絡間諜,關鍵基礎建設)
=======================================================================
=zh-TW&u=http://securityaffairs.co/wordpress/25070/cyber-crime/pla-officials-accused-hacking.html&usg=ALkJrhjqclhQ6zsH4HDZj3zvEjuVPMdchg
被指網絡間諜對美國公司5名中國解放軍官員

美國已提出刑事指控五名中國解放軍軍事官員網絡間諜和黑客對幾家美國公司。
美國本週初落案控告五名中國軍事解放軍軍官,並指控侵入美國公司的電腦他們 。 美國當局指控侵入美國公司在的中國的解放軍軍官能源部門竊取商業機密和知識產權。
美國司法部已發出新聞稿,其中透露的五個黑客,受害公司和網絡攻擊的時間段,下面從起訴書一個抽象的名字:
被告 :汪冬,孫楷亮,文新宇黃振宇和顧春暉,誰是在中國解放軍的第三處(PLA)的61398單位人員。 起訴書稱,王,孫,和溫家寶,以及其他已知和未知的大陪審團,黑客攻擊或試圖侵入在起訴書命名,而黃, 顧支持他們的陰謀,除其他事項外,基礎設施管理美國實體 (例如域帳戶),用於黑客攻擊。美國聯邦調查局指控解放軍官方的黑客和應用總量31計數收費 ,為:
受害人 :西屋電氣公司(西屋),太陽能世界公司(SolarWorld公司),美國鋼鐵公司(美國鋼鐵),阿勒格尼技術公司(ATI),美國鋼鐵,造紙和林業,橡膠,製造業,能源美國子公司 ,有關工業和服務人員國際工會(USW)和美國鋁業公司
時間週期 :2006-2014年。
- 陰謀犯的計算機欺詐和濫用
- 訪問(或試圖獲得),受保護的計算機未經授權獲取信息的商業利益和個人經濟利益的目的,
- 發送程序,信息,代碼或命令,意圖造成損害受保護的計算機
- 加重身份盜竊
- 經濟間諜活動
- 商業秘密盜竊
“當一個外國國家使用軍事或情報的資源和工具,對美國的行政人員或公司,以獲得商業秘密或敏感的商業信息,其國有企業的利益,我們必須說,'夠了',”美國司法部長埃里克·霍爾德宣布在新聞發布會上。
隨行的起訴書指出:
“從至少在或大約2006年直至並包括至少在我們對2014年4月,在人民解放軍的成員(”解放軍“),中國人民共和國的軍隊(”中國“),串謀和與對方攻入西區賓夕法尼亞州和其他地方的美國商業實體的電腦。“
中國政府否認了這些指控,稱這起事件會破壞關係,兩國。 網絡間諜活動是兩國政府最高國家安全的擔憂,T 運美國情報官員公佈的2014年年初新的 全球威脅評估報告 在參議院聽證會上,該文件考慮了外國進行網絡活動的影響 國家支持的黑客攻擊 ,作為國土安全構成嚴重威脅。

美國當局懷疑黑客解放軍的工作單位61398總部設在上海,據調查,黑客已經竊取商業秘密,也涉及到核電廠的設計和太陽能電池板公司的成本和價格數據的敏感數據。
聯邦檢察官懷疑目標公司的名單很長,包括美國鋁業公司,阿勒格尼技術公司,美國鋼鐵公司,東芝單元西屋電氣公司,太陽能世界公司的美國子公司 ,以及鋼鐵工人工會根據美國官員的損失該公司是“顯著。”
“受害人不得不對他們的中國競爭對手提起的所有不公平的貿易索賠,幫助華盛頓畫出所謂的黑客活動及其對國際業務的影響之間的聯繫。” 路透社報導 。
五解放軍çhinese官員被美國當局,國際逃犯認為,起訴書是一個明確的信息,其他政府,美國不希望接受其公司進一步網絡間諜活動,好奇,如果我們考慮基於文件的斯諾登最近披露在美國的網絡間諜活動針對國外。
請注意報導在起訴書中的文字,“ 起訴書僅僅是指控,被告人被推定為無罪,除非證明有罪的法庭。”
中國
不斷增長的影響力在該地區。新一代領導習近平是在地方,其雄心勃勃的政策
議程進入重點:加快推進經濟改革,使管理更加高效,
負責,並擰緊共產黨紀律。
中國可能將繼續其越來越積極的態度,海事糾紛,包括強硬
立場對日本在尖閣諸島。更廣泛地說,中國不斷增長的信心,新的
能力,和其他認知挑戰中國的利益和安全將推動北京追求
更積極的外交政策。
越來越多的領土爭端區域競爭和相互競爭的民族主義情緒增加風險
升級和制約區域合作。主權問題和歷史復活
怨恨會產生在華東和華南申索人之間的摩擦和偶爾的事件
中國海洋慢或失速雙邊或多邊努力來解決糾紛。
北京凸顯其追求“新型大國關係”的華盛頓,但中國是
同時工作至少間接地制衡美國的影響力。在東亞,北京
======================================
國家支持的黑客攻擊

匿名和國家資助的黑客威脅著能源行業

能源部門是威脅與黑客行動主義者,國家資助的黑客和網絡犯罪分子越來越頻繁......
對網絡攻擊的數量能源領域增加創建安全社區內的高度關注。 石油和天然氣公司都受到黑客行動主義者,搬到連續攻勢國家資助的攻擊秒,他們的活動是至關重要的任何國家,因為這個原因被認為是特權的目標。匿名例如正進行被稱為一個新的運動OpPetrol抗議的世界資源西方的統治。 該黑客行動主義者抗議能源部門採用美元作為貨幣的石油交易所。
“為什麼這個作品? 由於汽油銷售與美元和沙特阿拉伯已經背叛了穆斯林與他們的合作。 那麼,為什麼沒有汽油,其中出口是該國的貨幣賣“匿名的集體恫嚇的企業在能源領域與新的網絡攻擊浪潮,黑客可進行分佈式拒絕服務( DDoS攻擊 )攻擊,竊取公司系統敏感信息披露過程中收集的攻擊敏感信息,污損自己社交媒體帳戶和網站,但主要風險是與破壞的關鍵系統,特別是可能製作的惡意軟件 。
這是一場沒有國界,來自網絡空間的攻擊,將針對企業在不同的國家,如英國,美國,沙特阿拉伯,科威特和卡塔爾,加拿大,以色列,中國,俄羅斯和其他許多國家的能源部門工作。
繼由匿名提供目標的列表:
該操作似乎瞄準了以下國家:
- 美國
- 加拿大
- 英格蘭
- 以色列
- 中國
- 意大利
- 法國
- 俄羅斯
- 德國
- SUADIA ARABIA
- 科威特
- 卡塔爾
- 殼牌
- 沙特阿美公司
- 英國Petrolium
- 總
- 德士古
為企業,邀請他們要格外警惕相伴的運動開始。
“賽門鐵克建議將在未來幾天的攻擊做好準備的組織。 組織應在其網絡監測不尋常的活動,特別是任何試圖違反周長“匿名說他們已經妥協大約一千網站,35000認證電子郵件和超過10萬Facebook賬戶作為這項運動的一部分。 雖然匿名威脅石油和天然氣行業,許多其他可疑的攻擊擊中,根據伊朗石油部的計算機網絡梅爾新聞社。
“工作人員應經過專門培訓的社會工程學手段緩解以及定期的安全意識培訓。 與往常一樣,我們繼續強調重視實施多層次的方法來防守。“
用來感染系統中的特定的惡意軟件是一種後門木馬被稱為Cycbot,這使得使之成為一個巨大的一部分受害者殭屍網絡竊取後已停用正在系統上運行的安全處理敏感信息。 殺毒軟件和防火牆,因此,不足以保護自己。
該機構透露,襲擊有興趣的伊朗石油部,伊朗國家石油公司和其他一些公司都失敗了。 基礎設施據報導下來,由於網絡攻擊,但沒有信息已被洩露,並沒有破壞成功。
伊朗能源部門由外國政府,試圖破壞它不斷的攻擊,類似的攻擊進行了針對伊朗石油部去年四月和五月間。 在2010年最引人注目的襲擊伊朗的設施時, Stuxnet蠕蟲來破壞國家鈾濃縮計劃。
2011年4月,伊朗政府宣布,網絡間諜惡意軟件被稱為星病毒,第二劑的流行惡意軟件後,為了這個目的,襲擊該國發現的Duqu與Stuxnet蠕蟲病毒。
為了應對這些攻擊,確保網絡空間的安全,政府宣布成立網絡空間的最高委員會。
這些事件顯示出敵對政府的能源部門國家支持操作的極大興趣,如伊朗的。 從防禦的角度來看的威脅,必須在相同的角度來分析,無論其來源。 從攻擊者的角度來看國家資助的黑客,黑客行動主義者和網絡罪犯的伴隨動作可以促進彼此。
主要的惡意代理的源代碼是地下市場上很容易容易找到,這些惡意軟件可以利用上述各演員打隱藏犯罪的真正動機和attachers性質的目標。 使用這些碼可以有利的狀態下的選擇發起攻擊中的分集操作的更精密劑的擴散,同時罪犯和黑客行動主義可以有所有必要的攻擊策略目標,而無需特定的知識。
大多數工業化國家的能源部門仍然太容易受到網絡攻擊,但什麼是真正令人擔心的是必要的知識水平,造成了嚴重的破壞,美國政府最近公佈的報告顯示 ,該國的關鍵基礎設施易受網絡攻擊並且所有必要的攻擊者可以在互聯網上。
網絡安全是一個必須為任何政府,不僅為能源領域。
皮耶路易吉帕格尼尼
( 安全事務 -網絡安全,能源行業)
*Pierluigi Paganini*

########################################
http://melodytoyssexy.blogspot.com/2014/09/bytribalchief-information-security.html
======================================================================
**--Please use Google with a
large family of God translator to translate your country / language city Oh ^ ^
--請各位用家善用谷歌大神的翻譯器,來翻譯你們的國家/城市的語言喔^^
--Por favor, use o Google com
uma grande familia de Deus tradutor para traduzir sua cidade pais / idioma Oh ^
^
--** - 국가 / 언어 시 를 번역하는 하나님 번역기 의 큰 가족과 함께 구글을 사용하십시오 아 ^ ^
--S'il vous plait utilisez
Google avec une grande famille de Dieu traducteur pour traduire votre ville de
pays / langue Oh ^ ^
--Bitte verwenden Sie Google
mit einer grosen Familie Gottes Ubersetzer zu Ihrem Land / Sprache ubersetzen
Stadt Oh ^ ^
--*** - あなたの国/言語の街を翻訳する神トランスレータの大きなファミリーでGoogleを使用してくださいああ^ ^
** - Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--** - Utilice Google con una
gran familia de Dios traductor para traducir tu ciudad país / idioma Oh ^ ^
** - Si prega di utilizzare
Google con una grande famiglia di Dio traduttore per tradurre la tua città paese / lingua Oh ^ ^
--Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--Bonvole uzu Google kun
granda familio de Dio tradukisto traduki via lando / lingvo urbon Ho ^ ^

---By*tribal*Chief Information Security Officer Pierluigi Paganini*disclose share-*China Comment crew into taking over fake water "- and *accused of cyber espionage against U.S. companies five Chinese People's Liberation Army officials *- ---由*首席信息安全官部落*皮耶路易吉帕格尼尼*透露分享--*中國評論船員陷入接管假水廠"--和*被指網絡間諜對美國公司5名中國解放軍官員*- ---*부족*최고 정보 보안 책임자 Pierluigi 파가니니*이 주 공개함으로써- "가짜 물 위에 복용으로*중국 주석 승무원 -그리고*미국에 대한 사이버 스파이 혐의로 기소 회사 오 중국 인민 해방군 관리*- **USA/UK/TW/MACAU(FDZ)/KOREN/......all the world city lauguage**
===Melody.Blog===THE END===>/
&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&




沒有留言:
張貼留言
if you like make fds, wellcome you here~~anytime***
my free place for everyones who want the good software,
come & download them~ wellcome!!