''"Speaking recently on the Apple network of Chinese Communist Left Next Media glue (morbid) faction hacker attacks,
Mainland Chinese military prisoners bucket (not human rights take place step) or be forced to threaten researchers spyware.Internal and external uneasy, greedy Xi Jinping is Piru Soviet doctrine and practice growth.''The madness of inferiority mad, very much like the play the role of a clown ... "~ hehe .. ridiculed .. ''-
- Made me think of this monitoring Chinese people's new arguments article---
** DNS pollution incident tracking: Why cn and org domain names escaped ** -. -
- Made me think of this monitoring Chinese people's new arguments article---
** DNS pollution incident tracking: Why cn and org domain names escaped ** -.
"説到近日對蘋果網絡壹傳媒的中國共產左膠(病態)派黑客攻擊,
中國內地軍方的囚鬥(沒人權踏出位子一步)或被迫脅硏究間諜軟件.
對內對外的不安心,貪婪的習近平是被辱蘇聯主義的操練而成長,
這個瘋癲的自卑狂,極像戲中的小丑角色..."~嘿嘿..恥笑..-
- 令我想到這篇監控中國人的新論點文章,---
**DNS污染事件跟踪:为什么.cn和.org域名逃过一劫**--
"중공 왼쪽 다음 미디어 풀 (병적 인) 진영의 해커 공격의 애플 네트워크에 최근에 말하기,
중국 본토 군 포로 양동이 (인간의 권리는 위 단계를 수행하지 않음) 또는 연구원은 스파이웨어 위협하는 강제.
내부 및 외부 불안, 욕심 시진핑은 매우 광대의 역할은 ... "~ 헤헤 .. 조롱 놀이처럼, PIRU 소련의 교리와 실천 성장 '미친 열등감의 광기이다 ..'. -
- --- 날이 모니터링 중국 사람들의 새로운 인수 기사를 생각했다
* DNS 오염 사건 추적 : CN 및 조직 도메인 이름은 ** 탈출 이유 -.
"Falando recentemente na rede da Apple de chineses cola comunista Esquerda Próxima Mídia (mórbida) ataques de facção de hackers,
China Continental prisioneiros militares balde (não os direitos humanos ocorrem passo) ou ser forçado a ameaçar pesquisadores spyware.
Interna e externa inquieto, ganancioso Xi Jinping é doutrina Piru Soviética e crescimento prática'' A loucura de inferioridade louco, muito parecido com o jogo o papel de um palhaço ... "~ hehe .. ridicularizado ..''. -
- Me fez pensar em novo artigo argumentos Esta monitorização do povo chinês.
---** Rastreamento poluição DNS incidente: Por que os nomes de domínio cn e org escapou ** -.
''「中国共産党左次のメディアグルー(病的)派閥ハッカーの攻撃のアップルネットワークで最近話して、
本土中国軍捕虜のバケットは(人権は、プレース歩を踏み出すれていない)か、研究者がスパイウェアに脅威を余儀なくされる。
内部と外部の不安、貪欲習近平は非常に多くの道化師の役割は..."〜笑..嘲笑遊びのようなピルソ連の教義と実践の成長''狂った劣等狂気である..''。 -
- ---私は、この監視を中国の人々の新しい引数の記事を考えさせられた
**のDNS汚染事故の追跡:なぜCNおよびorgのドメイン名がエスケープさ** - 。
"Parolante ĵus sur la Pomo reto de ĉina komunisto Maldekstra Sekva Media gluo (malgaja) frakcio hacker atakoj,
Ĉeftero ĉinaj militaj malliberuloj sitelo (ne homajn rajtojn okazi paŝo) aŭ devigita minaci esploristoj spyware......''-
- Made me think of this monitoring Chinese people's new arguments article---
** DNS pollution incident tracking: Why cn and org domain names escaped ** -.
"説到近日對蘋果網絡壹傳媒的中國共產左膠(病態)派黑客攻擊,
中國內地軍方的囚鬥(沒人權踏出位子一步)或被迫脅硏究間諜軟件.
對內對外的不安心,貪婪的習近平是被辱蘇聯主義的操練而成長,
這個瘋癲的自卑狂,極像戲中的小丑角色..."~嘿嘿..恥笑..-
- 令我想到這篇監控中國人的新論點文章,---
**DNS污染事件跟踪:为什么.cn和.org域名逃过一劫**--
"중공 왼쪽 다음 미디어 풀 (병적 인) 진영의 해커 공격의 애플 네트워크에 최근에 말하기,
중국 본토 군 포로 양동이 (인간의 권리는 위 단계를 수행하지 않음) 또는 연구원은 스파이웨어 위협하는 강제.
내부 및 외부 불안, 욕심 시진핑은 매우 광대의 역할은 ... "~ 헤헤 .. 조롱 놀이처럼, PIRU 소련의 교리와 실천 성장 '미친 열등감의 광기이다 ..'. -
- --- 날이 모니터링 중국 사람들의 새로운 인수 기사를 생각했다
* DNS 오염 사건 추적 : CN 및 조직 도메인 이름은 ** 탈출 이유 -.
"Falando recentemente na rede da Apple de chineses cola comunista Esquerda Próxima Mídia (mórbida) ataques de facção de hackers,
China Continental prisioneiros militares balde (não os direitos humanos ocorrem passo) ou ser forçado a ameaçar pesquisadores spyware.
Interna e externa inquieto, ganancioso Xi Jinping é doutrina Piru Soviética e crescimento prática'' A loucura de inferioridade louco, muito parecido com o jogo o papel de um palhaço ... "~ hehe .. ridicularizado ..''. -
- Me fez pensar em novo artigo argumentos Esta monitorização do povo chinês.
---** Rastreamento poluição DNS incidente: Por que os nomes de domínio cn e org escapou ** -.
''「中国共産党左次のメディアグルー(病的)派閥ハッカーの攻撃のアップルネットワークで最近話して、
本土中国軍捕虜のバケットは(人権は、プレース歩を踏み出すれていない)か、研究者がスパイウェアに脅威を余儀なくされる。
内部と外部の不安、貪欲習近平は非常に多くの道化師の役割は..."〜笑..嘲笑遊びのようなピルソ連の教義と実践の成長''狂った劣等狂気である..''。 -
- ---私は、この監視を中国の人々の新しい引数の記事を考えさせられた
**のDNS汚染事故の追跡:なぜCNおよびorgのドメイン名がエスケープさ** - 。
"Parolante ĵus sur la Pomo reto de ĉina komunisto Maldekstra Sekva Media gluo (malgaja) frakcio hacker atakoj,
Ĉeftero ĉinaj militaj malliberuloj sitelo (ne homajn rajtojn okazi paŝo) aŭ devigita minaci esploristoj spyware......''-*
*
**--Please use Google with a
large family of God translator to translate your country / language city Oh ^ ^
--請各位用家善用谷歌大神的翻譯器,來翻譯你們的國家/城市的語言喔^^
--Por favor, use o Google com
uma grande familia de Deus tradutor para traduzir sua cidade pais / idioma Oh ^
^
--** - 국가 / 언어 시 를 번역하는 하나님 번역기 의 큰 가족과 함께 구글을 사용하십시오 아 ^ ^
--S'il vous plait utilisez
Google avec une grande famille de Dieu traducteur pour traduire votre ville de
pays / langue Oh ^ ^
--Bitte verwenden Sie Google
mit einer grosen Familie Gottes Ubersetzer zu Ihrem Land / Sprache ubersetzen
Stadt Oh ^ ^
--*** - あなたの国/言語の街を翻訳する神トランスレータの大きなファミリーでGoogleを使用してくださいああ^ ^
** - Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--** - Utilice Google con una
gran familia de Dios traductor para traducir tu ciudad país / idioma Oh ^ ^
** - Si prega di utilizzare
Google con una grande famiglia di Dio traduttore per tradurre la tua città paese / lingua Oh ^ ^
--Sila gunakan Google dengan
keluarga besar penterjemah Tuhan untuk menterjemahkan bandar negara / bahasa
anda Oh ^ ^
--Bonvole uzu Google kun
granda familio de Dio tradukisto traduki via lando / lingvo urbon Ho ^ ^
Chinese domain name resolves to 65.49.2.178 What is a mistake?
Chinese domain name resolves to 65.49.2.178 What is a mistake? Let's find out.
The first part describes the accident
China is a DNS service provider DNSPOD in at 4:18 p.m. on January 21, 2014, said:
January 21, 2014 in the afternoon around 15:10, DNSPod find the root of all domestic gTLDs abnormal, technical staff has contacted the relevant agencies to coordinate treatment. Currently root has returned to normal, but will follow the following problems:
Although the root of recovery, but there are IP address returns an
error, because the country has a cache, so some areas may last 12 hours.
The following is a screenshot of some friends in the accident available online:
The second part of the IP data areas to find a cause
All domestic generic top-level domain, is resolved to 65.49.2.178. Many large-scale failures nationwide website domain name is resolved to 65.49.2.178, which is what IP? http://www.ip.cn/index.php?ip=65.49.2.178 have the following four answers:
- GeoIP: Fremont, California, United States Hurricane Electric
- 65.49.2.178 = American town of Cary, North Carolina
- Dynamic Internet Technology Dynamic Internet Technology Company
- Anonymous Proxy
Sina science and technology,
n at 16:16 on January 21 2014 issued a document saying:
Sina Technology News on January 21 afternoon, according to a number of
DNS service provider revealed today 15:00, the root server all the
country gTLDs abnormal, leading to most domestic users can not properly
resolve domain names, causing the system to the national Internet link
impact.
Internet root servers mainly used to manage the home directory.
Only 13 units worldwide, which 13 root domain name servers are "A" to
"M", of which 10 units set up in the United States, in addition to each
one set in the United Kingdom, Sweden and Japan.
"Simply put, if we want to access this site baidu.com, first point to
the root server, then the user root service point. Com server,. Com
analytic server and then point users to baidu.com." One DNS technical
experts explained that this problem occurs only in China, indicating
that the global root servers are not a problem, the problem is likely to
be domestic network operators.
"This visit fault in 15:20 or so, when a user requests a root server is
pointing to an IP address (A record), which is completely wrong boot."
Experts said.
This is not the Chinese government's use of the domain name located in
China contaminated root DNS service do not accidentally get out of it a
mistake?
A few years ago my domain zuola.com GFW contamination ,
contamination of the domain name is known to the GFW fake IP are:
- 64.33.88.161 Trumbull, Connecticut, United States OLM, LLC
- 202.106.1.2 Beijing, China China Unicom Beijing
- 216.234.179.13 Edmonton, Alberta, Canada Tera-byte Dot Com
- 4.36.66.178 United State Level 3 Communications
- 211.94.66.147 Beijing, China
- 202.181.7.85 Australia
- 209.145.54.50 San Marcos, California, United States
The IP in the 2012 April 19 Sunrise now this website http://ffman.exteen.com/20110817/welfare-storm-ch2
Iran also appeared in a number of languages and Thai language
website, apparently this was as IP agent, may indeed be an anonymous
proxy (Anonymous Proxy) used IP.
Want to try to do reverse lookup for 65.49.2.178 parsing fails.
In the GOOGLE search 178.2.49.65.in-addr.arpa. Only one search result
http://dns.l4x.org/65.49.2.178, did not understand what it is, where it
appears from the IP information not found "state-sponsored DNS pollution
"evidence. http://whois.domaintools.com/65.49.2.178 And http://whois.arin.net/rest/nets;? q = 65.49.2.178 showDetails = true & showARIN = false & ext = netref2 Show this IP in Cheyenne, USA Sophidea Inc. United States Cheyenne Sophidea Inc.
In http://www.projecthoneypot.org/ip_65.49.2.178 showed that IP is actually 12 user-agent string
Dynamic Internet Technology Inc. is what company?
Used Freegate, circumvention tools unbounded people know that this is a
long-term blockade against the Chinese government, a technology company
Falun Gong websites, dynamic web publishing various circumvention
tools.
| IP | PTR | A |
|---|
| 65.49.2.9 |
| ultrasurf.us , ultrasurfing.com , wujieliulan.com |
| 65.49.2.10 |
| blogwujie.com , wujieblog.com |
| 65.49.2.13 |
| cbzs.info , jqzx.info |
| 65.49.2.28 |
| feitian-california.org |
| 65.49.2.29 |
| symail.org , synewsletter.com |
| 65.49.2.41 |
| epochdaily.com |
| 65.49.2.101 |
| bet888win.com , clgtchat.com , crystalprofit.net ,
eachother.biz , EVA-funds.biz , freeantiddos.com ,
Kaplan-properties.com , lizafund.com ,
Profit-finance.com , proxy1.idealhosting.org ,
proxy2.idealhosting.org , rekario.com ,
texinkarbotu.com , torrenubosa.com |
| 65.49.2.112 |
| ns1.freeantiddos.com |
| 65.49.2.114 |
| ns2.freeantiddos.com |
| 65.49.2.153 |
| dns.chinese1.org |
| 65.49.2.208 |
| fgmtv.org |
| 65.49.2.216 |
| fgmtv.net , hotdownload.org |
| 65.49.2.247 |
| pudumail.com , shenyunmail.org , sycircle.com |
| 65.49.2.253 |
| weiboleak.com |
This shows that the IP is indeed freedom doors circumvention tools used IP. In other words, you can put this incident and the Chinese government's Internet blockade operations linked.
I checked the IP and IP 65.49.2.178 segment is located, is a dynamic
network for anonymous proxy honeypot project to be detected before, but
this IP is not bound to any domain name, does not provide services over
the web, you can not reverse analysis , is guided in the past does not
exist GFW generate DDoS attack effect argument. http://whois.webhosting.info/65.49.2.178
The third part of the root name servers to find a cause
I try to come to terms from the root name servers.
I have the impression that at least one root server in China,
but Tencent said in a report this incident :
The main root server used to manage the home directory of the Internet, the world is only 13 units. A main root server, placed in the United States.
The remaining 12 were supplemented by the root servers, including nine
placed in the United States, Europe 2, in the UK and Sweden, the Asian
one, located in Japan.
All root servers authorized by the U.S. government with the Internet
Assigned Numbers Authority ICANN Uniform Domain Name Management,
responsible for the global Internet domain name root servers, domain
name system and IP address management.
Wikipedia also said, " Chinese root server is shut down . " This gives the impression that foreign root name server is wrong. I think it is wrong, the Chinese mainland F, I these two root domain DNS server mirroring.
October 2003 in Beijing installed a F-root server, October: F-Root installed in Beijing, People's Republic of China;
In 2006, China introduced within the root name servers J-ROOT and
top-level domain servers B-gTLD top level domain server mirroring;
ICANN root name servers in 78 cities have more than 120 nodes, there
are three nodes in Beijing, which is the root name server mirroring:
-
F-ROOT (telecommunications, switching center) by the Internet Software
Alliance (ISC = Internet Systems Consortium) and China Telecom jointly
established.
- J-ROOT (CNC) and China Netcom jointly established by Verisign.
-
I-ROOT (CNNIC) was established by the Swedish National Internet
Exchange (Autonomatic, later called Netnod company) in the CNNIC.
In the F-root Asia-Pacific region had 14 mirror image below from the Asia Pacific Network Information Center:
Because China has a root name
server node, so the "DNS round-trip cycle (or called the ring trip time
Round Trip Time)" The RTT algorithm guarantees that after a period of
DNS polling time will choose the fastest response within the root domain
after "learning" server.
And this is just a site failure occurs in China, showing the massive
site failure culprit is China's root name server mirroring.
Next, is to identify which of several of China's real IP address root
name server, and then test to see if these servers work properly.
However, Wikipedia says:
"Chinese mainland F, I root domain DNS these two mirror [9], but
because of multiple DNS pollution and the impact of foreign networks,
threatening the safety and freedom of the Internet was disconnected from
the Internet."
According to Wikipedia, I found this story in English: " After DNS problem, Chinese root Server is shut Dow
N ", says the link in the" 'withdrawn route announcements' made by
the server ", sounds like China is still China root mirror, Swedish
company Netnod just withdrawn route announcements with the server, not
canceled mirror, right?
I want to track the IP 192.5.5.241 in Beijing where, for the first time actually in the United States:
traceroute to 192.5.5.241 (192.5.5.241), 64 hops max, 72 byte packets
1 192.168.10.1 (192.168.10.1) 1.247 ms 1.114 ms 1.078 ms
2 192.168.1.1 (192.168.1.1) 1.481 ms 1.354 ms 1.313 ms
3 h × × ×. S98.ts.hinet.net (168.95.98. × × ×) 7.286 ms 7.455 ms 7.190 ms
4 * h242.s25.ts.hinet.net (168.95.25.242) 7.473 ms 7.358 ms
5 tpdt-3012.hinet.net (220.128.4.30) 21.033 ms * 13.669 ms
6 ***
7 ** r4001-s2.tp.hinet.net (220.128.11.133) 10.042 ms
8 * 211-72-108-153.hinet-ip.hinet.net (211.72.108.153) 144.699 ms 144.337 ms
9 paix.r1.pao1.isc.org (198.32.176.3) 145.071 ms * 145.100 ms
10 f.root-servers.net (192.5.5.241) 144.551 ms 144.491 ms 144.794 ms
The IP 198.32.176.3 recent U.S. IP.
The second is connected to the Jiangsu again with VPN traceroute
traceroute to 192.5.5.241 (192.5.5.241), 64 hops max, 72 byte packets
1 1.1.1.1 (1.1.1.1) 112.112 ms 108.556 ms 108.587 ms
2 221.6.170.1 (221.6.170.1) 119.476 ms 118.213 ms 113.267 ms
3 221.6.161.153 (221.6.161.153) 112.413 ms 118.053 ms 122.491 ms
4 221.6.161.201 (221.6.161.201) 119.346 ms 121.014 ms 114.563 ms
5 219.158.96.149 (219.158.96.149) 150.785 ms 150.258 ms 154.764 ms
6 219.158.4.10 (219.158.4.10) 147.241 ms 147.273 ms 147.740 ms
7 * 219.158.97.254 (219.158.97.254) 213.981 ms 205.347 ms
8 219.158.102.154 (219.158.102.154) 334.414 ms 330.767 ms *
9 las-bb1-link.telia.net (213.248.94.125) 505.146 ms 326.467 ms 316.009 ms
10 dls-bb1-link.telia.net (213.248.80.14) 361.110 ms 490.916 ms 360.979 ms
11 chi-bb1-link.telia.net (80.91.248.208) 404.532 ms 416.520 ms 454.820 ms
12 isc-117366-chi-bb1.telia.net (213.248.85.18) 456.797 ms 465.479 ms 468.200 ms
13 f.root-servers.net (192.5.5.241) 532.196 ms 494.677 ms 423.665 ms
The results show first went to Jiangsu, Liaoning, and then to China
Unicom, and then from f.root-servers.net recent 80.91.248.208 and
213.248.85.18 is actually the European IP. Look for the anycast
technology (anycast) is mirrored on the behavior of IP routing
protocols, an IP address corresponding to multiple servers, so the
servers in Europe and the United States have.
Then I asked Shao held in China tracert help me look at this F-ROOT root name servers
C: \ Users \ chensh aoju> tracert 192.5.5.241
By tracking up to 30 hops to f.root-servers. NET [192.5.5.241] route:
1
4 ms 17 ms 4 ms 10.20.0.1 2 6 ms 4 ms 4 ms 4 ms 10.20.0.1 3 23 ms 10 ms
5 ms 58.215.135.21 4 11 ms 11 ms 31 ms 31 ms 61.177.102.13 5 32 ms 202.97.65.201 6 *** Request timed out. 7 32 ms 32 ms 33 ms 18.254.120.106. static.bjteleco m.net [106.120.254 .18] 8 42 ms 34 ms 32 ms 219.142.18.54 9 31 ms 32 ms 33 ms 218.241.102.101 10 30 ms 39 ms 33 ms 218.241.107.90 11 30 ms 72 ms 32 ms f.root -servers. NET [192.5.5.241]
Tracking complete.
Well, this time from the nearest 192.5.5.241 IP 218.241.107.90 is a CNNIC's IP, can prove F-ROOT still in China, says Wikipedia wrote " Chinese root server is shut down , "is wrong.
Here only found CNNIC's F-ROOT, in accordance with the foregoing
argument, there should be a China Telecom's F-ROOT, China Telecom's IP
may need to check to get the F-ROOT position.
J-ROOT also in Beijing:
C: \ Users \ chensh aoju> tracert 192.58.128.30
By tracking up to 30 hops to j.root-servers. NET [192.58.128.30] route:
1
5 ms 3 ms 3 ms 10.20.0.1 2 4 ms 4 ms 3 ms 5 ms 10.20.0.1 3 24 ms 9 ms
58.215.156.185 4 7 ms 5 ms 6 ms 58.215.156.185 5 10 ms 9 ms 7 ms 202.97.39.113 6 8 ms 11 ms 11 ms 26 ms 202.97.48.30 7 27 ms 26 ms 219.158.32.93 8 33 ms 32 ms 31 ms 219.158.13.21 9 30 ms 40 ms 30 ms 30 ms 123.126.0.66 10 * 11 138 * 61.51.112.42 134 ms 136 ms 37 ms 33 ms 61.148.156.202 12 ms 33 ms bt-235-194.bta. net.cn [202.106.235.19 4] 13 25 ms 36 ms 32 ms j.root-Servers. NET [192.58.128.30] Trace complete.
tracert I-ROOT's IP actually went to Japan to run:
Another server
Or go to Japan, it seems with Wuxi Telecom, Beijing and Henan CNLink
network access are unable to prove that the i-root not in China. According Yiming said:
Where I node in 2010 because of GFW failure to return overseas
contaminated dns records who had been yelled at, administrators all over
the world and they cried nothing interested can looking through the old
stories https://lists .dns-oarc.net/pipermail/dns-operations/2010-March/005260.html
It seems I-Root node in trouble since 2010 after the close
international route advertisement, has not radio, no wonder the country
is also used to track tracert less than i-root node.
The first tracert L-ROOT of IP also ran to Japan, estimated to be living in Wuxi Chan Siu move faster to visit Japan. The second change Henan server:
This got a China's L-ROOT, and from the L-ROOT recent 61.49.41.74 is --
Currently proven F-ROOT, J-ROOT, L-ROOT has mirrored in Beijing, China. In http://www.root-servers.org on this page to search Beijing, displays F, I, J, L four server
has a mirror in Beijing, China.
Currently, there are 13 sets of root name servers, which the United
States 10, Europe 2 (in the United Kingdom and Sweden), Asia 1 (in
Japan), and in the global deployment of over 300 service nodes root
mirror in China There are five mainland, covering F, I, J, L roots.
Where, F root causes ISC (Internet Systems Consortium) agency
cooperation and CNNIC, the Beijing construction of two F-root mirror
service nodes, respectively, by providing network access to China
Telecom and CNNIC; Verisign cooperation with China Unicom, the
construction of the J roots in Beijing mirror server, China Unicom to
provide access.
The other two provide network room environment by the CNNIC are to
cooperate with Netnod, ICANN, built in Beijing I, L root mirror service
node. At present, China still relevant bodies to continue international cooperation and the implementation of more root mirror node.
Say so on the right, F-ROOT two, I-ROOT, J-ROOT and L-ROOT each one,
CNNIC's F-ROOT found, but China Telecom's F-ROOT not found in China,
I-ROOT I have no way to prove that in China. Which perhaps readers can find tracert look, if you can find trouble tracert results posted under it.
I found gtld-servers also 13, I thought with the F-ROOT these have anything to do with it, this b.gtld-servers. Beijing also seems to have a net:
C: \ Users \ chensh aoju> tracert 192.33.14.30
By tracking up to 30 hops to b.gtld-servers. NET [192.33.14.30] route:
1
8 ms 5 ms 7 ms 10.20.0.1 2 3 ms 3 ms 5 ms 10.20.0.1 3 7 ms 7 ms 6 ms
61.177.102.105 4 5 ms 4 ms 6 ms 61.177.102.105 5 8 ms 7 ms 7 ms 202.97.39.233 6 15 ms 11 ms 11 ms 98 ms 202.97.48.42 7 94 ms 96 ms 219.158.35.89 8 134 ms 134 ms 214 ms 219.158.5.217 9 70 ms 34 ms 32 ms 38 ms 123.126.0.70 10 * 11 37 * 124.65.56.18 ms 29 ms 30 ms 40 ms 37 ms 61.148.6.42 12 36 ms bt-235-194.bta. net.cn [202.106.235.19 4] 13 36 ms 51 ms 45 ms b.gtld-Servers. NET [192.33.14.30]
Tracking complete.
From b.gtld-servers.net recent IP 202.106.235.194 is China Unicom.
The question now is, do not know in the territory of China F, I, J, L
five root name servers,
as well as similar b.gtld-servers.net such a
top-level domain DNS server has done in terms of pollution, but
reasonable suspicion China's DNS root servers dishonesty, evidence in
the following two links, this incident took place in 2010:
In 2010, the Netherlands Online reports that " Chinese Internet censorship trial out of the border accidentally . "
March 24, a Domain Name System (DNS) management staff in Chile found
that abnormal flow of Internet information to Youtube, Twitter, Facebook
access requirements were hijacked to China issued fake websites and IP
addresses.
This link
also said foreign Internet users get an IP address from the root name
servers Twitter China after contamination, Facebook, YouTube's.
Part IV Conclusion
DNS query process introduced --
Next encounter similar to today's root domain name service returns a false IP address how to verify it? I recommend the following steps:
-
First determine the F-ROOT, I-ROOT, J-ROOT, L-ROOT's IP survive in
Chinese territory, the methodology is tracert several mirror IP, their
IP is globally uniform, but mapping multiple hosts, you have to Confirm
your network from the nearest root domain host is online. IP hosts to which the root domain to find http://www.internic.net/domain/named.root
- Open a command line, type nslookup
- Then enter the set q = PTR
- Enter the server 192.5.5.241
- Just enter a. Com domain name, such as zuola.com
- At this time the results will return a string of authoritative answer should tell you where: Authoritative answers can be found from:
com nameserver = h.gtld-servers.net.
com nameserver = j.gtld-servers.net.
com nameserver = k.gtld-servers.net.
com nameserver = g.gtld-servers.net.
com nameserver = m.gtld-servers.net.
com nameserver = i.gtld-servers.net.
com nameserver = c.gtld-servers.net.
com nameserver = f.gtld-servers.net.
com nameserver = a.gtld-servers.net.
com nameserver = d.gtld-servers.net.
com nameserver = e.gtld-servers.net.
com nameserver = b.gtld-servers.net.
com nameserver = l.gtld-servers.net.
a.gtld-servers.net internet address = 192.5.6.30
b.gtld-servers.net internet address = 192.33.14.30
c.gtld-servers.net internet address = 192.26.92.30
d.gtld-servers.net internet address = 192.31.80.30
e.gtld-servers.net internet address = 192.12.94.30
f.gtld-servers.net internet address = 192.35.51.30
g.gtld-servers.net internet address = 192.42.93.30
h.gtld-servers.net internet address = 192.54.112.30
i.gtld-servers.net internet address = 192.43.172.30
j.gtld-servers.net internet address = 192.48.79.30
k.gtld-servers.net internet address = 192.52.178.30
l.gtld-servers.net internet address = 192.41.162.30
m.gtld-servers.net internet address = 192.55.83.30
a.gtld-servers.net has AAAA address 2001:503: a83e :: 2:30
- Enter the server 192.5.6.30
- Enter zuola.com
- This returns Server: 192.5.6.30
Address: 192.5.6.30 # 53
Non-authoritative answer:
*** Can't find zuola.com: No answer
Authoritative answers can be found from:
zuola.com nameserver = ns1.dreamhost.com.
zuola.com nameserver = ns2.dreamhost.com.
ns1.dreamhost.com internet address = 66.33.206.206
ns2.dreamhost.com internet address = 208.96.10.221
- The above results returned contains the real domain and nameserver IP, enter the server 66.33.206.206
- Return> server 66.33.206.206
Default server: 66.33.206.206
Address: 66.33.206.206 # 53
- Enter the set q = a
- Enter zuola.com
- Return> zuola.com
Server: 66.33.206.206
Address: 66.33.206.206 # 53
Name: zuola.com
Address: 69.163.141.215
- Thus, it found the real IP is 69.163.141.215 the domain zuola.com
The first step to find the nearest root domain first, the second step
to return gTLD root domain name address, the third step gTLD name server
returns the address and IP, the fourth step name server returns the
real IP domain.
ROOT Server returns which gTLD domain name should go to find, gTLD a
recent server tells you on which DNS server (name server) records of
your domain name corresponding to the IP, the server also registered
gTLD domain name server (name server) domain and the real IP, in my
case, ns1.dreamhost.com 66.33.206.206 information on the record and in
gtld-servers.net A to M's 13 servers. DNS clearer description of this chart parsing process below:
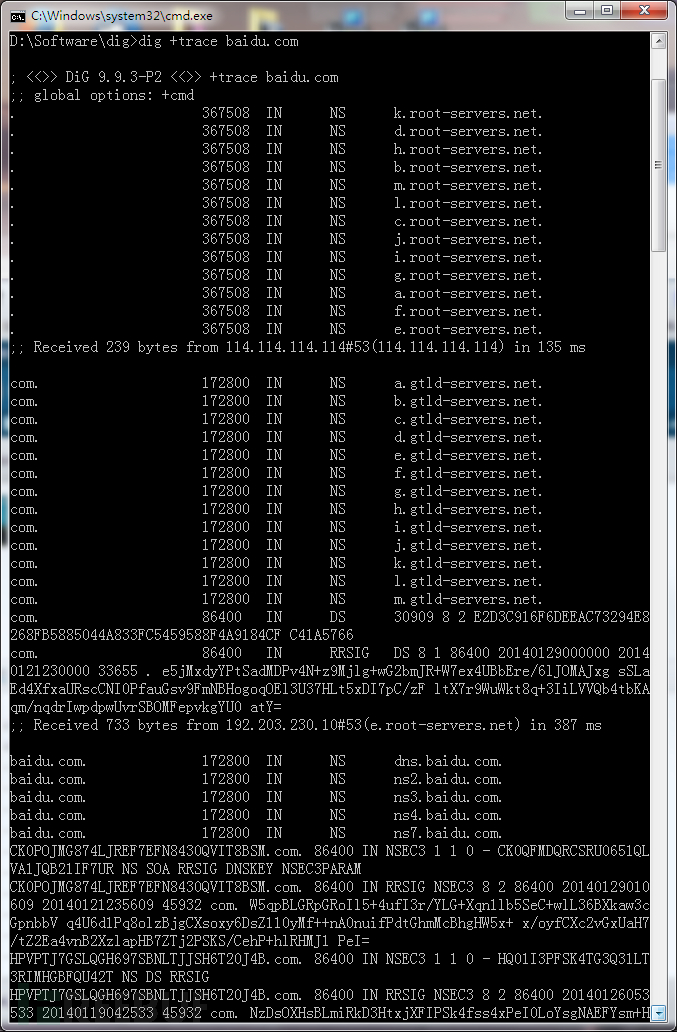
At 15:00 on January 21, 2014 about the operation but did not dig on the
second and third steps in Fig return gTLD server and the name server
process, skip this part of the name server returns the address of an
65.49.2.178, the following two plans are no gTLD servers appear, there
is no name server, which returns with a very short delay 65.49.2.178
this fake IP. The first figure shows only 27 milliseconds, the second chart shows only 36 milliseconds. 

My understanding is that there is a room of GFW on the border router,
the UDP DNS queries result of contaminated normal, due to the passing
GFW, it returns a false IP. A few years ago in China GFW only outbound traffic pollution DNS query results, the flow must be GFW room now examined.
My conclusion is that this is a DNS pollution incidents within China,
is an attempt to examine the device in the engine room of the GFW block
when doing a network made honest mistake (unintentional mistakes
committed), may be the door to block IP freedom to operate block all
domain names.
===========================================================
*中國的域名解析到65.49.2.178 是一個什麼失誤?
中國的域名解析到65.49.2.178 是一個什麼失誤? 讓我們來查一查。
第一部分事故描述
中國的一家DNS 服務商DNSPOD於2014年1月21日16:18說:
2014年1月21日下午15:10左右,DNSPod發現國內所有通用頂級域的根出現異常,技術人員已聯繫相關機構協調處理。 目前根已恢復正常,但是後續還會存在以下問題:
根雖已恢復,但還有返回錯誤IP地址,因為各地有緩存,所以部分地區可能會持續12小時。
以下是一些網友在網上提供的事故截圖:
第二部分從IP資料方面找原因
國內所有通用的頂級域名,被解析到65.49.2.178。 全國大規模網站故障許多域名被解析到65.49.2.178,這是一個什麼IP? http://www.ip.cn/index.php?ip=65.49.2.178有下面四種答案:
- GeoIP: Fremont, California, United States Hurricane Electric
- 65.49.2.178=美國北卡羅萊納州卡里鎮
- Dynamic Internet Technology 動態互聯網技術公司
- Anonymous Proxy
新浪科技的《 中國頂級域名根服務器故障大部分網站受影響 》在
2014年01月21日16:16發文說:
新浪科技訊1月21日下午消息,據多家DNS服務商透露,今日下午3點,全國所有通用頂級域的根服務器出現異常,導致國內大部分用戶無法正確解析域名,對全國互聯網鏈接造成系統性影響。
根服務器主要用來管理互聯網的主目錄。 全世界只有13台,這13台根域名服務器中名字分別為“A”至“M”,其中10台設置在美國,另外各有一台設置於英國、瑞典和日本。
“簡單的說,如果我們要訪問baidu.com這個網站,先要指向根服務器,根服務再將用戶指向.com服務器,.com的解析服務器再把用戶指向
baidu.com。”一位DNS技術專家解釋說,這次的問題僅出現在中國,說明全球根服務器並未出現問題,問題很可能是國內網絡運營商。
“這次訪問故障出現在下午3點20分左右,當用戶請求根服務器時,被指向一個IP地址(A記錄),這是完全錯誤的引導。”上述專家表示。
這是不是中國政府利用位於中國的域名根服務做DNS污染時不小心弄出來的一個失誤呢?
前些年我的域名zuola.com被GFW污染 ,所已知GFW對域名污染的給的假IP有:
- 64.33.88.161 Trumbull, Connecticut, United States OLM, LLC
- 202.106.1.2 Beijing, China China Unicom Beijing
- 216.234.179.13 Edmonton, Alberta, Canada Tera-byte Dot Com
- 4.36.66.178 United State Level 3 Communications
- 211.94.66.147 Beijing, China
- 202.181.7.85 澳大利亞
- 209.145.54.50 San Marcos, California, United States
這個IP在2012年04月19日出現在這個網頁上 http://ffman.exteen.com/20110817/welfare-storm-ch2
也出現在一些伊朗語言和泰國語言的網站上,顯然這個IP曾被當成代理,可能確實是一個匿名代理(Anonymous Proxy)用過的IP .
想嘗試對65.49.2.178 做反向解析,解析失敗。
在GOOGLE搜索178.2.49.65.in-addr.arpa. 只有一條搜索結果http://dns.l4x.org/65.49.2.178 ,沒看懂是什麼,從IP信息裡看來找不到“國家支持的DNS污染”的證據。 http://whois.domaintools.com/65.49.2.178 和 http://whois.arin.net/rest/nets;q=65.49.2.178?showDetails=true&showARIN=false&ext=netref2 顯示這個IP在美國夏延市Sophidea Inc. United States Cheyenne Sophidea Inc.
在http://www.projecthoneypot.org/ip_65.49.2.178 顯示有這個IP居然12個user-agent 字符串
Dynamic Internet Technology公司是個什麼公司? 用過自由門、無界的翻牆工具的人都知道,這是對抗中國政府長期封鎖法輪功網站的一家技術公司,在動態網上發佈各種翻牆工具。
可以看到動態網公司的網站都在這個65.49.2.0/24的IP段上:
| IP | PTR | A |
|---|
| 65.49.2.9 |
| ultrasurf.us , ultrasurfing.com , wujieliulan.com |
| 65.49.2.10 |
| blogwujie.com , wujieblog.com |
| 65.49.2.13 |
| cbzs.info , jqzx.info |
| 65.49.2.28 |
| feitian-california.org |
| 65.49.2.29 |
| symail.org , synewsletter.com |
| 65.49.2.41 |
| epochdaily.com |
| 65.49.2.101 |
| bet888win.com , clgtchat.com , crystalprofit.net ,
eachother.biz , eva-funds.biz , freeantiddos.com ,
kaplan-properties.com , lizafund.com ,
profit-finance.com , proxy1.idealhosting.org ,
proxy2.idealhosting.org , rekario.com ,
texinkarbotu.com , torrenubosa.com |
| 65.49.2.112 |
| ns1.freeantiddos.com |
| 65.49.2.114 |
| ns2.freeantiddos.com |
| 65.49.2.153 |
| dns.chinese1.org |
| 65.49.2.208 |
| fgmtv.org |
| 65.49.2.216 |
| fgmtv.net , hotdownload.org |
| 65.49.2.247 |
| pudumail.com , shenyunmail.org , sycircle.com |
| 65.49.2.253 |
| weiboleak.com |
可見這個IP確實是自由門等翻牆工具用過的IP。
也就是說,可以把這個事故和中國政府的網絡封鎖操作聯繫起來。
我查過65.49.2.178 這個IP和所在的IP段,是動態網用於匿名代理,
被蜜罐項目偵測到過,但這個IP沒有綁定任何域名,未提供過web服務,
我嘗試從根域名服務器方面來找。
我印像中,至少有一台根服務器在中國,但騰訊網在報導此次事件時說 :
根服務器主要用來管理互聯網的主目錄,全世界只有13台。 1個為主根服務器,放置在美國。 其餘12個均為輔根服務器,其中9個放置在美國,歐洲2個,位於英國和瑞典,亞洲1個,位於日本。 所有根服務器均由美國政府授權的互聯網域名與號碼分配機構ICANN統一管理,負責全球互聯網域名根服務器、域名體系和IP地址等的管理。
維基百科上也說“ 中國根服務器被關閉 ”。 這樣給人印像是國外根域名服務器有錯。 我覺得不對, 中國大陸有F、I這2個根域DNS服務器鏡像。
2003年十月就在北京安裝了一個F-root服務器,October: F-Root installed in Beijing, People's Republic of China;
2006年,中國境內引進根域名服務器J-ROOT和頂級域名服務器B-gTLD頂級域名服務器鏡像;
ICANN的根域名服務器在78個城市有120多個節點為,在北京有三個節點,也就是根域名服務器鏡像:
- F-ROOT(電信,交換中心)由互聯網軟件聯盟(ISC=Internet Systems Consortium)和中國電信共同建立。
- J-ROOT(網通) 由Verisign和網通共同設立。
- I-ROOT(CNNIC) 由瑞典國家互聯網交換中心(Autonomatic,後來叫Netnod公司)在CNNIC設立。
在亞太地區的F-root就有14個鏡像,下面這張圖來自亞太互聯網絡信息中心:
由於在中國有根域名服務器節點,所以“域名解析往返週期(或叫環程時間Round Trip Time)"的RTT算法會保證經過一段DNS輪詢時間“學習”後會選擇響應最快的境內根域名服務器。 並且此次僅有中國大陸出現網站故障,可見此次大規模網站故障的罪魁禍首是中國的根域名服務器鏡像。
接下來,就是要找出中國的這幾台根域名服務器的真實IP地址,然後測試一下這幾台服務器是否正常工作。
不過維基百科上說:
“中國大陸有F、I這2個根域DNS鏡像[9],但因為多次發生DNS污染而影響外國網絡,威脅互聯網安全和自由而被斷開與國際互聯網的連接。”
我想跟踪192.5.5.241 這個IP在北京哪裡,第一次居然是在美國:
traceroute to 192.5.5.241 (192.5.5.241), 64 hops max, 72 byte packets
1 192.168.10.1 (192.168.10.1) 1.247 ms 1.114 ms 1.078 ms
2 192.168.1.1 (192.168.1.1) 1.481 ms 1.354 ms 1.313 ms
3 h×××.s98.ts.hinet.net (168.95.98.×××) 7.286 ms 7.455 ms 7.190 ms
4 * h242.s25.ts.hinet.net (168.95.25.242) 7.473 ms 7.358 ms
5 tpdt-3012.hinet.net (220.128.4.30) 21.033 ms * 13.669 ms
6 * * *
7 * * r4001-s2.tp.hinet.net (220.128.11.133) 10.042 ms
8 * 211-72-108-153.hinet-ip.hinet.net (211.72.108.153) 144.699 ms 144.337 ms
9 paix.r1.pao1.isc.org (198.32.176.3) 145.071 ms * 145.100 ms
10 f.root-servers.net (192.5.5.241) 144.551 ms 144.491 ms 144.794 ms
最近的這個IP 198.32.176.3是美國IP。
第二次用VPN連到江蘇再traceroute
traceroute to 192.5.5.241 (192.5.5.241), 64 hops max, 72 byte packets
1 1.1.1.1 (1.1.1.1) 112.112 ms 108.556 ms 108.587 ms
2 221.6.170.1 (221.6.170.1) 119.476 ms 118.213 ms 113.267 ms
3 221.6.161.153 (221.6.161.153) 112.413 ms 118.053 ms 122.491 ms
4 221.6.161.201 (221.6.161.201) 119.346 ms 121.014 ms 114.563 ms
5 219.158.96.149 (219.158.96.149) 150.785 ms 150.258 ms 154.764 ms
6 219.158.4.10 (219.158.4.10) 147.241 ms 147.273 ms 147.740 ms
7 * 219.158.97.254 (219.158.97.254) 213.981 ms 205.347 ms
8 219.158.102.154 (219.158.102.154) 334.414 ms 330.767 ms *
9 las-bb1-link.telia.net (213.248.94.125) 505.146 ms 326.467 ms 316.009 ms
10 dls-bb1-link.telia.net (213.248.80.14) 361.110 ms 490.916 ms 360.979 ms
11 chi-bb1-link.telia.net (80.91.248.208) 404.532 ms 416.520 ms 454.820 ms
12 isc-117366-chi-bb1.telia.net (213.248.85.18) 456.797 ms 465.479 ms 468.200 ms
13 f.root-servers.net (192.5.5.241) 532.196 ms 494.677 ms 423.665 ms
結果顯示先跑到江蘇,然後到遼寧聯通,然後離f.root-servers.net最近的80.91.248.208和213.248.85.18居然是歐洲IP。 看為任播技術(anycast)是IP路由協議上的鏡像行為,一個IP地址對應多個服務器,所以這個服務器在歐洲和美國都有。
然後我拜託陳少舉幫我在中國境內tracert一下這個F-ROOT根域名服務器
C:\Users\chensh aoju>tracert 192.5.5.241
通過最多30個躍點跟踪到 f.root-servers. net [192.5.5.241]的路由:
1
4 ms 17 ms 4 ms 10.20.0.1 2 6 ms 4 ms 4 ms 10.20.0.1 3 23 ms 4 ms 5 ms
58.215.135.21 4 10 ms 11 ms 11 ms 61.177.102.13 5 31 ms 31 ms 32 ms 202.97.65.201 6 * * *請求超時。 7 32 ms 32 ms 33 ms 18.254.120.106. static.bjteleco m.net [106.120.254 .18] 8 42 ms 34 ms 32 ms 219.142.18.54 9 31 ms 32 ms 33 ms 218.241.102.101 10 30 ms 39 ms 33 ms 218.241.107.90 11 30 ms 72 ms 32 ms f.root -servers. net [192.5.5.241]
跟踪完成。
好,這回離192.5.5.241最近的IP 218.241.107.90是一個CNNIC的IP,可以證明F-ROOT還在中國,維基百科上說寫的“ 中國根服務器被關閉 ”是錯的。 這裡只查到CNNIC的F-ROOT,按照前文的說法,應該還有一個中國電信的F-ROOT,也許需要中國電信的IP才能查得到這個F-ROOT的位置。
J-ROOT也在北京:
C:\Users\chensh aoju>tracert 192.58.128.30
通過最多30個躍點跟踪到 j.root-servers. net [192.58.128.30]的路由:
1
5 ms 3 ms 3 ms 10.20.0.1 2 4 ms 4 ms 3 ms 10.20.0.1 3 24 ms 5 ms 9 ms
58.215.156.185 4 7 ms 5 ms 6 ms 58.215.156.185 5 10 ms 9 ms 7 ms 202.97.39.113 6 8 ms 11 ms 11 ms 202.97.48.30 7 27 ms 26 ms 26 ms 219.158.32.93 8 33 ms 32 ms 31 ms 219.158.13.21 9 30 ms 40 ms 30 ms 123.126.0.66 10 * 30 ms * 61.51.112.42 11 138 ms 134 ms 136 ms 61.148.156.202 12 37 ms 33 ms 33 ms bt-235-194.bta. net.cn [202.106.235.19 4] 13 25 ms 36 ms 32 ms j.root-servers. net [192.58.128.30]跟踪完成。
tracert I-ROOT的IP居然跑日本去了:
換個服務器
還是去日本了,看來用無錫電信、北京互聯通和河南的網絡接入均無法證明i-root在不在中國。 據宮一鳴說:
其中I節點在2010年的GFW故障中因為給海外返回被污染的dns記錄曾被人罵得狗血噴頭,管理員滿世界哭訴和他們無關,有興趣的可以翻翻這個陳年舊事https://lists .dns-oarc.net/pipermail/dns-operations/2010-March/005260.html
看來I-Root節點自從2010年在國際上闖禍後就關閉路由通告了,一直沒廣播,難怪在國內也用tracert追踪不到i-root節點。
第一次tracert L-ROOT的IP也跑日本去了,估計是陳少舉住的無錫訪問日本更快。 第二次換河南服務器:
目前,全球共有13台套根域名服務器,其中美國10個,歐洲2個(位於英國和瑞典)、亞洲1個(位於日本),並在全球部署有三百多個根鏡像服務節點,在中國大陸地區有5個,覆蓋了F、I、J、L 根。 其中,F 根由ISC(Internet Systems Consortium)機構與CNNIC合作,在北京建設了兩個F根鏡像服務節點,由中國電信和CNNIC分別提供網絡接入;Verisign與中國聯通合作,在北京建設了J根鏡像服務器,中國聯通提供接入。 另外兩個由CNNIC提供網絡機房環境分別與Netnod、ICANN合作,在北京建設了I、L根鏡像服務節點。 目前中國還有相關機構繼續與國際合作實施更多的根鏡像節點。
這樣說就對了,F-ROOT有兩個,I-ROOT、J-ROOT和L-ROOT各一個,CNNIC的F-ROOT找到了,但中國電信的F-ROOT沒在中國找到,I-ROOT我也沒有辦法證明在中國。 也許哪位讀者可以tracert一下找到,若能找到,麻煩貼下tracert結果吧。
我發現gtld-servers也是13個,我以為跟F-ROOT這些有什麼關係呢,這個 b.gtld-servers. net 好像也在北京有一份:
C:\Users\chensh aoju>tracert 192.33.14.30
通過最多30個躍點跟踪到 b.gtld-servers. net [192.33.14.30]的路由:
1
8 ms 5 ms 7 ms 10.20.0.1 2 3 ms 3 ms 5 ms 10.20.0.1 3 7 ms 7 ms 6 ms
61.177.102.105 4 5 ms 4 ms 6 ms 61.177.102.105 5 8 ms 7 ms 7 ms 202.97.39.233 6 15 ms 11 ms 11 ms 202.97.48.42 7 94 ms 98 ms 96 ms 219.158.35.89 8 134 ms 134 ms 214 ms 219.158.5.217 9 70 ms 34 ms 32 ms 123.126.0.70 10 * 38 ms * 124.65.56.18 11 37 ms 29 ms 30 ms 61.148.6.42 12 40 ms 37 ms 36 ms bt-235-194.bta. net.cn [202.106.235.19 4] 13 36 ms 51 ms 45 ms b.gtld-servers. net [192.33.14.30]
跟踪完成。
離b.gtld-servers.net 最近的IP 202.106.235.194 是聯通的。 現在的問題是,不知道在中國境內的F、I、J、L這五個根域名服務器,還有類似b.gtld-servers.net 這樣的頂級域名服務器在污染DNS方面做了些什麼,不過可以合理懷疑中國的DNS根服務器不誠實,證據在下面兩個鏈接中,這個事件發生在2010年:
2010年,有荷蘭在線報導說《 中國網絡審查一不小心審出了國境 》
3月24日,智利的一名域名解析系統(DNS)管理人員發現互聯網信息流通出現異常,向Youtube、Twitter、Facebook發出的訪問要求均被劫持到中國的假網站和IP地址。
這個鏈接也說外國網絡用戶得到了來自這個中國根域名服務器污染後的Twitter、Facebook、YouTube的IP地址。
第四部分結論
DNS查詢過程介紹
下次遇到類似今天的根域名服務返回假IP地址時如何查證呢? 我建議步驟如下:
- 先確定F-ROOT、I-ROOT、J-ROOT、L-ROOT的IP存活於中國境內,方法就是tracert這幾個鏡像的IP,他們的IP是全球統一的,但映射多個主機,你要確認離你網絡最近的根域名主機是在線的。 根域名主機的IP到這找http://www.internic.net/domain/named.root
- 打開命令行,輸入nslookup
- 然後輸入set q=PTR
- 輸入server 192.5.5.241
- 隨便輸入一個.com的域名,如zuola.com
- 此時會返回一串結果告訴你權威回答應該會在哪裡: Authoritative answers can be found from:
com nameserver = h.gtld-servers.net.
com nameserver = j.gtld-servers.net.
com nameserver = k.gtld-servers.net.
com nameserver = g.gtld-servers.net.
com nameserver = m.gtld-servers.net.
com nameserver = i.gtld-servers.net.
com nameserver = c.gtld-servers.net.
com nameserver = f.gtld-servers.net.
com nameserver = a.gtld-servers.net.
com nameserver = d.gtld-servers.net.
com nameserver = e.gtld-servers.net.
com nameserver = b.gtld-servers.net.
com nameserver = l.gtld-servers.net.
a.gtld-servers.net internet address = 192.5.6.30
b.gtld-servers.net internet address = 192.33.14.30
c.gtld-servers.net internet address = 192.26.92.30
d.gtld-servers.net internet address = 192.31.80.30
e.gtld-servers.net internet address = 192.12.94.30
f.gtld-servers.net internet address = 192.35.51.30
g.gtld-servers.net internet address = 192.42.93.30
h.gtld-servers.net internet address = 192.54.112.30
i.gtld-servers.net internet address = 192.43.172.30
j.gtld-servers.net internet address = 192.48.79.30
k.gtld-servers.net internet address = 192.52.178.30
l.gtld-servers.net internet address = 192.41.162.30
m.gtld-servers.net internet address = 192.55.83.30
a.gtld-servers.net has AAAA address 2001:503:a83e::2:30
- 輸入server 192.5.6.30
- 輸入zuola.com
- 此時返回Server: 192.5.6.30
Address: 192.5.6.30#53
Non-authoritative answer:
*** Can't find zuola.com: No answer
Authoritative answers can be found from:
zuola.com nameserver = ns1.dreamhost.com.
zuola.com nameserver = ns2.dreamhost.com.
ns1.dreamhost.com internet address = 66.33.206.206
ns2.dreamhost.com internet address = 208.96.10.221
- 上面返回的結果裡包含了真正的nameserver的域名和IP,輸入server 66.33.206.206
- 會返回> server 66.33.206.206
Default server: 66.33.206.206
Address: 66.33.206.206#53
- 輸入set q=a
- 輸入zuola.com
- 返回> zuola.com
Server: 66.33.206.206
Address: 66.33.206.206#53
Name: zuola.com
Address: 69.163.141.215
- 這樣,就查到域名zuola.com 的真實IP為69.163.141.215 了
第一步先是找到最近的根域名,第二步根域名返回gTLD地址,第三步gTLD返回name server地址和IP,第四步name server返回域名的真實IP。
ROOT Server返回域名應該去哪個gTLD找,gTLD提供一個最近的服務器告訴你哪個域名解析服務器(name
server)上記錄了你的域名對應的IP,gTLD的服務器上亦登記了域名解析服務器(name
server)的域名和真實IP,在我的例子中,ns1.dreamhost.com和66.33.206.206的信息就記錄在gtld-
servers.net的A到M的13台服務器上。 下面這張圖更清晰的描述的DNS解析過程:
2014年1月21日下午3點左右的dig操作卻沒有上圖的第二步和第三步返回gTLD server和name server過程,直接跳過name
server這個環節返回了一個65.49.2.178的地址,下面兩張圖都沒有gTLD服務器出現,也沒有name
server,所用延時極短就返回65.49.2.178這個假IP。 第一張圖顯示只用了27毫秒,第二張圖顯示只用了36毫秒。 

我的理解是,機房的邊界路由器上有一個GFW,把正常查詢DNS的UDP結果污染了,由於要路過GFW,所以返回了一個假的IP。 前些年GFW只在中國出境流量上污染DNS查詢結果,現在機房流量也要被GFW審查了。 我的結論是,這是一次中國境內的DNS污染事故,是嘗試在機房的GFW審查設備做網絡封鎖時做出的honest mistake(無意犯下的過錯),可能是封鎖自由門的IP時操作成封鎖所有域名了。
===========================================================
*DNS pollution incident tracking: Why cn and escaped org domain
User
access on the territory of China. Com and. Net domain name resolves to
65.49.2.178 issue I have a new discovery, I found out why. Cn and. Org
domain pointing 65.49.2.178 not affected by the cause of accidents and
prove this independent of root name servers.
In the last article
, I found the IP 65.49.2.178 this background, the root name server to
verify the mirror in China, refuted the major media and Wikipedia says
"root name server has only 13 units, the only one in Asia Taiwan in
Japan, "saying, guess DNS pollution accidents from this incident was a
domestic engine room.
I noticed CNCERT notice
mentioned only ". com", ". net" sites, such as the end of the affected,
and. cn end of the site was not affected,. org end of the site is not
mentioned, but also should not be affected:
Bulletin on January 21 unusual circumstances our country's Internet access
Source: CNCERT Time :2014-01-22
At 15:20 on January 21, 2014, the territory of a large number of
Chinese Internet users can not access the domain name with ". Com", ".
Net" such as the end of the site.
After the incident, the National Internet Emergency Center launched the
emergency response mechanism for the first time, part of the technical
support organization to coordinate the investigation and emergency
response units, around 16:50, user access returned to normal.
Was to analyze the available data, the initial judge the incident was
due to cyber attacks resulting in the territory of China Internet users
top level domain service through an exception when the international
resolve to attack the source is under further investigation.
Why. Cn and. Org site is not affected by the end?
Let's look at a normal name resolution process:
- The first step, DNS will return to the "root name servers" address and IP, the above figure is the root-servers.net the end of the address;
- The second step, the root name server 192.33.4.12 return gTLDs (gTLD) server addresses and IP;
- The third step, gTLD server returns NS (name server) address and the IP, the above figure is ns1.dreamhost.com;
- The fourth step, NS return to the real IP address of the domain name corresponding to the figure above is 69.163.141.215.
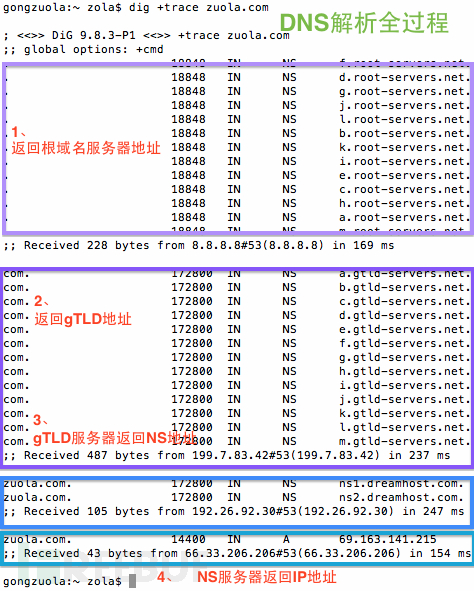
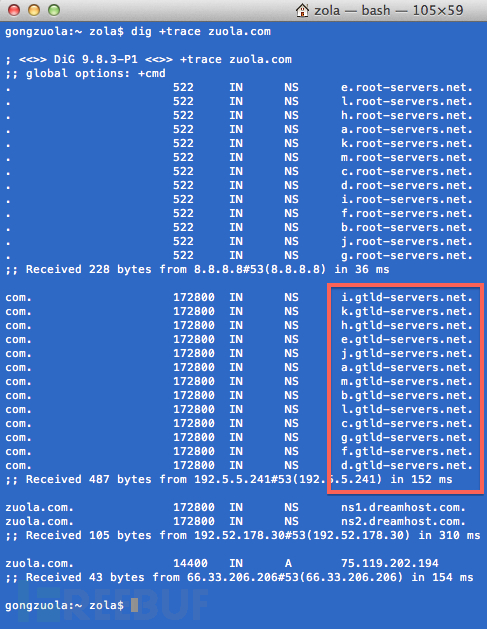
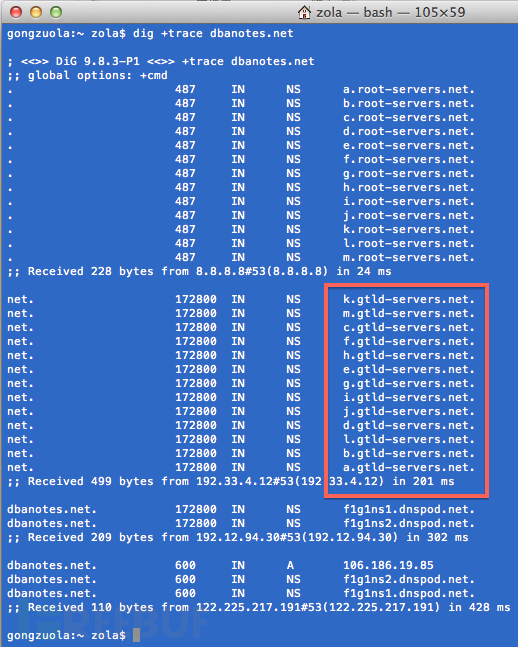
Here is the dig + trace zuola.com and dig + trace dbanotes.net result,
the displayed ". Com", ". Net" domain names ending in the second step,
such as the return of all gtld-server.net end server address ; while in
". org" domain using another domain name server.
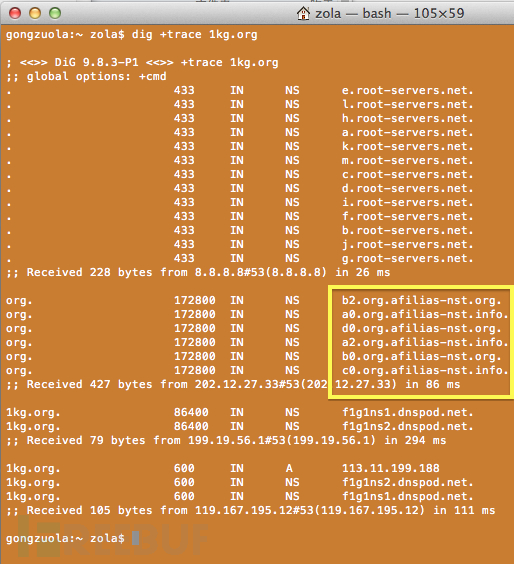
Here are the results of dig + trace 1kg.org this domain, we also need
to initiate the first step in DNS queries, the result returned is the
same root name server address, the
second step is not returned by the end of the server gtld-server.net
address, is org.afilias-nst.org and org.afilias-nst.info end of the
address
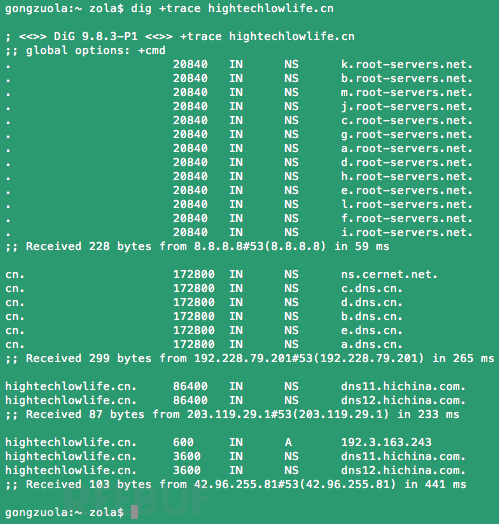
Here is the result dig + trace hightechlowlife.cn this domain name, cn,
and org domain names also need to initiate the first step to DNS
queries to get the correct root name server
addresses; .. The second step is not returned gtld-server . net at the
end of the server address, nor is org.afilias-nst.org and
org.afilias-nst.info the end of the address, end address is dns.cn:
Well,. Cn and. Org domain names also need to initiate the first step in
DNS queries, are also obtained. Com now. Net domain name the same "root name servers" query results, and only the second step to return a different result . This proves that the incident with the "root name servers" absolutely nothing. Such a distinction might be able to explain why. Cn and. Org domain name has not been affected.
The following chart from the BLOG DNSPod , confirmed January 21, 2014 Visit com domain will get 65.49.2.178 this IP.:
No Return Return gTLDs (gTLD) server address and IP, there is no return name server addresses.
No Return Return gTLDs (gTLD) server address and IP, there is no return name server addresses.
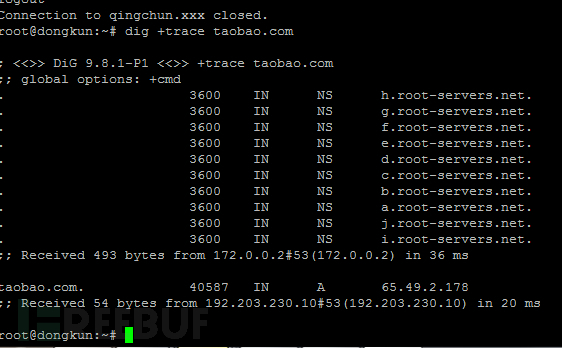
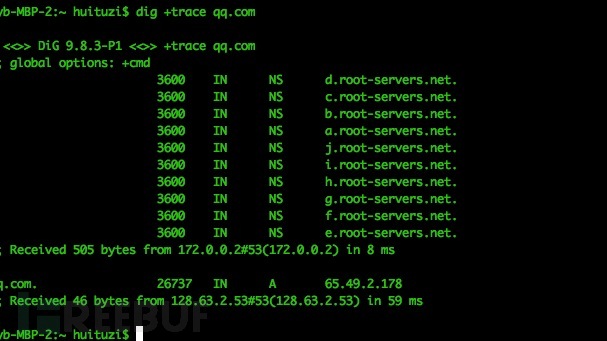
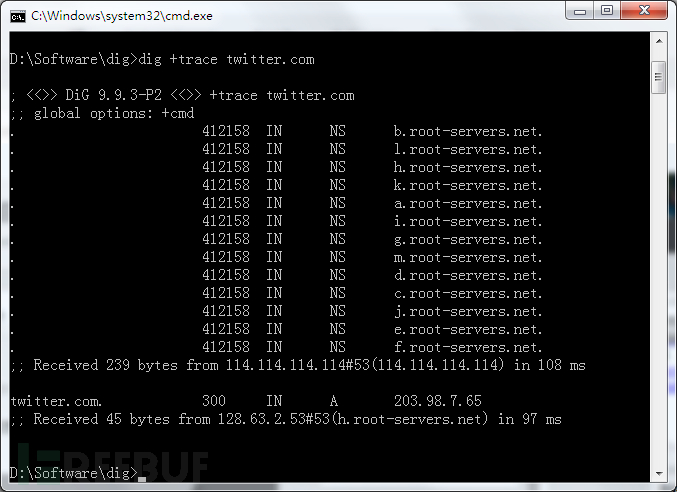
I put another track with a dig in China, Jan. 22, 2014 picture twitter.com domain name resolution process:
Twitter.com domain name was hijacked to 203.98.7.65 the IP, and from http://whois.webhosting.info/203.98.7.65
view, this IP is not twitter's IP, performance and hijack domain
January 21, 2014 in to 65.49.2.178 exactly the same: no return return
gTLDs (gTLD) server address and IP, there is no return name server
addresses.
Complete and correct analysis should be the same as shown in four return data:
In conclusion:
Exception occurs when Internet users within China through international
top-level domain analytical services, ". Com", ". Net" domain name
resolves to 65.49.2.178 is a DNS polluting behavior, and GFW pollution
Twitter.com, Facebook.com Youtube.com, Zuola.com domain names
performance is consistent with the root name servers completely unrelated.
. Cn and. Org end of the site is not affected if proved, may be the GFW
accidentally contaminated gtld-servers.net domain names added to the
list, the next encounter the same part of the domain name, then with the
use of the affected dig + trace gtld-servers.net to troubleshoot it.
These views are not necessarily absolutely correct, please add the possibility and evidence.
==============================================================
http://melodytoyssexy.blogspot.com/2014/07/speaking-recently-on-apple-network-of.html
*DNS污染事件跟踪:為什麼.cn和.org域名逃過一劫
關於中國境內用戶訪問.com 和.net 域名被解析到65.49.2.178 一事我又有新發現,我發現了為什麼.cn 和.org 的域名沒有受到影響指向65.49.2.178的原因,證明此事事故與根域名服務器無關。
在上一篇文章中,我查到了65.49.2.178這個IP的背景,驗證了根域名服務器在中國有鏡像,駁斥了各大媒體和維基百科上說“根域名服務器只有13台,亞洲唯一的一台在日本”的說法,猜測這事件是一次來自國內機房的DNS污染事故。
我注意到國家互聯網應急中心的通告提到僅有“.com”、“.net”等結尾的網站受到影響,而.cn結尾的網站沒有受到影響,.org結尾的網站沒有被提到,也應該是沒有受到影響:
關於1月21日我國境內互聯網訪問異常情況的通報
來源: CNCERT時間:2014-01-22
2014年1月21日15:20,中國境內大量互聯網用戶無法正常訪問域名以“.com”、“.net”等結尾的網站。 事件發生後,國家互聯網應急中心第一時間啟動應急響應機制,協調組織部分技術支撐單位進行調查和應急處置,16:50左右,用戶訪問基本恢復正常。
經對已掌握的數據進行分析,初步判斷此次事件是由於網絡攻擊導致我國境內互聯網用戶通過國際頂級域名服務解析時出現異常,攻擊來源正在進一步調查中。
為什麼.cn 和.org 結尾的網站沒有受到影響?
我們先來看正常的域名解析過程:
- 第一步,DNS會返回“ 根域名服務器 ”地址和IP,上圖中是root-servers.net結尾的地址;
- 第二步, 根域名服務器 192.33.4.12返回通用頂級域名(gTLD)的服務器地址和IP;
- 第三步,gTLD服務器返回NS(name server)地址和IP,上圖中是ns1.dreamhost.com;
- 第四步,NS返回域名對應的真正的IP地址, 上圖中是69.163.141.215。
下
面是dig +trace zuola.com 和dig +trace dbanotes.net
的結果,顯示以“.com”、“.net”等結尾的域名在第二步返回的都是gtld-server.net結尾的服務器地址;
而以“.org”的域名用的是另一種域名的服務器。
下面是dig +trace 1kg.org這個域名的結果,同樣需要向DNS發起第一步查詢,返回的結果是相同的根域名服務器地址,第二步返回的卻不是以gtld-server.net結尾的服務器地址,是org.afilias-nst.org 和org.afilias-nst.info 結尾的地址
下面是dig +trace hightechlowlife.cn這個域名的結果,.cn和.org的域名同樣需要向DNS發起第一步查詢,得到了正確的根域名服務器地址;第二步返回的卻不是以gtld-server .net結尾的服務器地址,也不是以org.afilias-nst.org 和org.afilias-nst.info 結尾的地址,是以dns.cn結尾的地址:
好了,.cn和.org的域名同樣需要向DNS發起第一步查詢,也都得到與.com跟.net域名相同的“ 根域名服務器 ”查詢結果了,僅有第二步返回的結果不同。 這證明此次事件與“根域名服務器”完全沒有關係。 這樣一區分,也許能解釋為什麼.cn 和.org 的域名沒有受到影響了。
沒有返回返回通用頂級域名(gTLD)的服務器地址和IP,也沒有返回name server地址。
沒有返回返回通用頂級域名(gTLD)的服務器地址和IP,也沒有返回name server地址。
我再貼一張2014年1月22日在中國境內用dig追踪twitter.com 域名解析過程的圖片:
完整無誤的解析應該是如下圖一樣分四次返回數據:
結論:
我
國境內互聯網用戶通過國際頂級域名服務解析時出現異常,“.com”、“.net”域名被解析到65.49.2.178是一次DNS污染行為,和GFW污
染Twitter.com 、Facebook.com Youtube.com 、 Zuola.com等域名的表現是一致的,與根域名服務器完全無關。 .cn 和.org 結尾的網站沒有受到影響則證明,可能是此次GFW不小心把gtld-servers.net 加入污染域名的列表了,下次遇到同樣的部分域名受影響的話用用dig +trace gtld-servers.net來排查吧。
以上觀點不一定絕對正確,歡迎補充可能性和證據。
原創文章: http://www.zhoushuguang.com/2014/01/root-servers.html
作者:佐拉http://weibo.com/zuola
*轉載請註明出自:FreebuF.COM*
''Among the essence dismantling fine exhaustive,
worth to play with "clown" ... Oh ... ~!! -
Play together, "Household" Chinese communist "clown",
he does not treat people kindly!
Which need to treat him as a man Oh -!! Hey ... hey ridiculed ... -
''當中精粹拆解精細無遺,值得拿來玩一下"小丑"...呵呵...~!!-
一起玩玩"家家酒"中國共產"小丑",他不仁慈對待人們!
哪需對待他如人喔!!-嘿...嘿恥笑...-
"광대"로 연주 할 가치가 철저한 벌금을 해체 본질 중 ... 아 ~!,
"생활"중공 "광대"함께! - 플레이,
''그는 친절하게 사람을 치료하지 않습니다!
"사람들이 오처럼 그를 치료하기 위해 필요한 것"!- 안녕 ... 안녕 조롱 .... -
''Entre a essência desmantelamento bem exaustivo, vale a pena jogar com o "palhaço" ... Oh ... ~! -Jogar juntos ", Household" comunista chinês "palhaço",
ele não tratar as pessoas gentilmente! "O que as pessoas precisam tratá-lo como Oh"!-Ei ... ei ridicularizado .... ''-
--''「ピエロ」でプレーする価値は、徹底的な細かい解体エッセンスの中で···ああ〜!一緒に! - 再生、"家庭"中国の共産主義"ピエロ"
彼は親切に人々を治療しません!"の人がああのように彼を治療するのに必要なもの"!- ちょっと...ちょっと嘲笑....'' -
'' Inter la esenco malmunti fajna ĝisfunda, valoras por ludi kun "pajaco" ... Ho ... ~!! -Ludi kune, "Household" ĉina komunista "pajaco",
li ne traktas popolon afable,
Kiu bezonas traktu lin kiel homo Ho -!! Hej ... hey ridindigis ... -
http://melodytoyssexy.blogspot.com/2014/07/speaking-recently-on-apple-network-of.html

*"Speaking recently on the Apple network of Chinese Communist Left Next Media glue (morbid) faction hacker attacks,
Mainland Chinese military prisoners bucket (not human rights take place step) or be forced to threaten researchers spyware.
Internal and external uneasy, greedy Xi Jinping is Piru Soviet doctrine and practice growth.''The madness of inferiority mad, very much like the play the role of a clown ... "~ hehe .. ridiculed .. ''-
- Made me think of this monitoring Chinese people's new arguments article---
** DNS pollution incident tracking: Why cn and org domain names escaped ** -.
"説到近日對蘋果網絡壹傳媒的中國共產左膠(病態)派黑客攻擊,
中國內地軍方的囚鬥(沒人權踏出位子一步)或被迫脅硏究間諜軟件.
對內對外的不安心,貪婪的習近平是被辱蘇聯主義的操練而成長,
這個瘋癲的自卑狂,極像戲中的小丑角色..."~嘿嘿..恥笑..-
- 令我想到這篇監控中國人的新論點文章,---
**DNS污染事件跟踪:为什么.cn和.org域名逃过一劫**--
"중공 왼쪽 다음 미디어 풀 (병적 인) 진영의 해커 공격의 애플 네트워크에 최근에 말하기,
중국 본토 군 포로 양동이 (인간의 권리는 위 단계를 수행하지 않음) 또는 연구원은 스파이웨어 위협하는 강제.
내부 및 외부 불안, 욕심 시진핑은 매우 광대의 역할은 ... "~ 헤헤 .. 조롱 놀이처럼, PIRU 소련의 교리와 실천 성장 '미친 열등감의 광기이다 ..'. -
- --- 날이 모니터링 중국 사람들의 새로운 인수 기사를 생각했다
* DNS 오염 사건 추적 : CN 및 조직 도메인 이름은 ** 탈출 이유 -.*
===Melody.Blog===THE END===>/

 *
*



 =================================================
=================================================